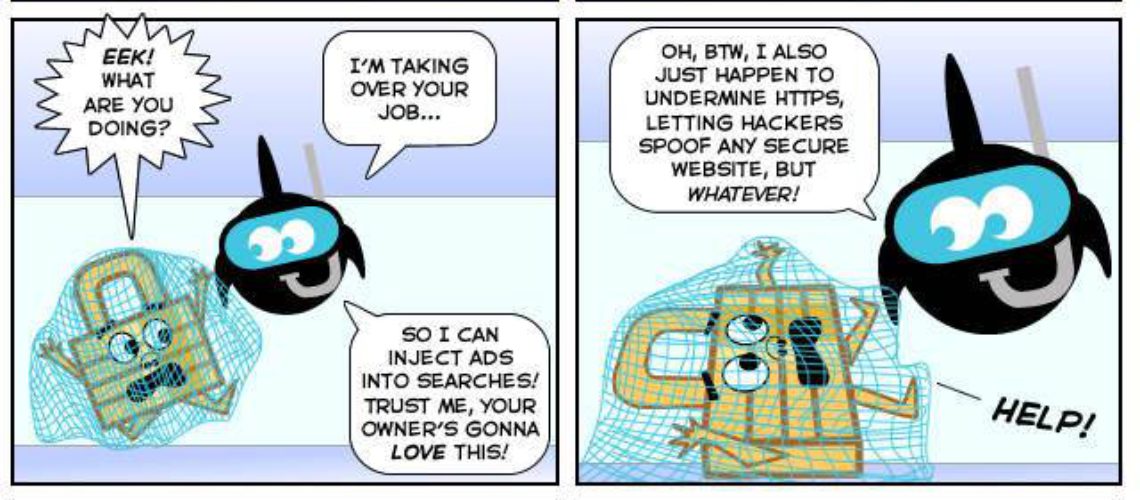
Many security companies are now providing detection routines for the Superfish browser add-on in the products they offer. This became a reality after the discovery that this add-on is relying on a self-signed root certificate in order to intercept encrypted traffic and gain access to information that is sensitive.
In the period between September and December 2014, the Superfish browser add-on came preloaded on numerous Lenovo laptops. That fact created quite a buzz once the researchers discovered that behavior of the add-on.
The Superfish browser add-on and its behavior
The add-on Superfish has been designed to present advertisements on the webpages that are accessed by the users in order to help them find alternative and cheaper products of the ones that they searched online. The add-on achieves that by running an image that is matching the algorithm on more than 70 000 stores found online.
How is that done? The Superfish add-on installs a transparent proxy service (also known as man-in-the-middle), which is based on the SSL Digestor engine by Komodia. That engine installs a root certificate in Windows store that is self-generated and then re-signs all HTTPS sites certificates on-the-fly. The website of Komodia is currently offline thanks to the serious attention form the media.
This set-up provides third-parties with access to information that should be encrypted in first place between the server and the client. Something that is even more striking is that is the RSA key for encryption of the certificate is cracked, the communication between the Superfish users can be revealed and the secure traffic exchange can be seen.
Last Thursday the CEO of Errata Security, Robert Graham, succeeded in cracking the password for the encrypted private key of the certificate. Soon, he also managed to find the password as well.
Alert for Superfish by several antivirus products
Until just recently, Superfish was accepted as a potentially unwanted program only that was set on the computers of the users along with the installation of some free applications. In fact there were online tutorials on how to remove that browser component; however it stayed undetected by most of the security products.
Even today the detection rate is low, even if the security solutions are now triggering alerts when they find Superfish. The popular antivirus products such as Avira, Symantec and Trend Micro issue a warning concerning that add-on, which is based on through reputation or heuristic engines or based on a signature.
The security bulletin further informs that the program removal is not enough in order to reduce the risk, since the users also need to uninstall the root certificate. Microsoft provides information on how to do that in the certificate store of Windows. The same is done my Mozilla for its Thunderbird email client and its Firefox web browser.