Recent reports from malware researchers inform that there is an increased number of hacked iOS apps. The cybercriminals are aware of the mobile apps popularity and in 2014 they have cloned approximately 87 % of the top paid apps for iOS and 97 % of the top paid software for Android devices. These numbers might be striking, however for the Android apps this result is considered an improvement since last year all top paid apps have been cloned to malicious versions spreading malware. The interest towards the apps for the iOS devices has risen with more than 30 %, which means that the cybercriminals are now also interested in the operating system of Apple.
The company Arxan Technology has made a research based on the hundred most downloaded applications that are paid for the two platforms. It also searched for their rogue counterparts on third-party app stores, torrent trackers and various websites for distribution.
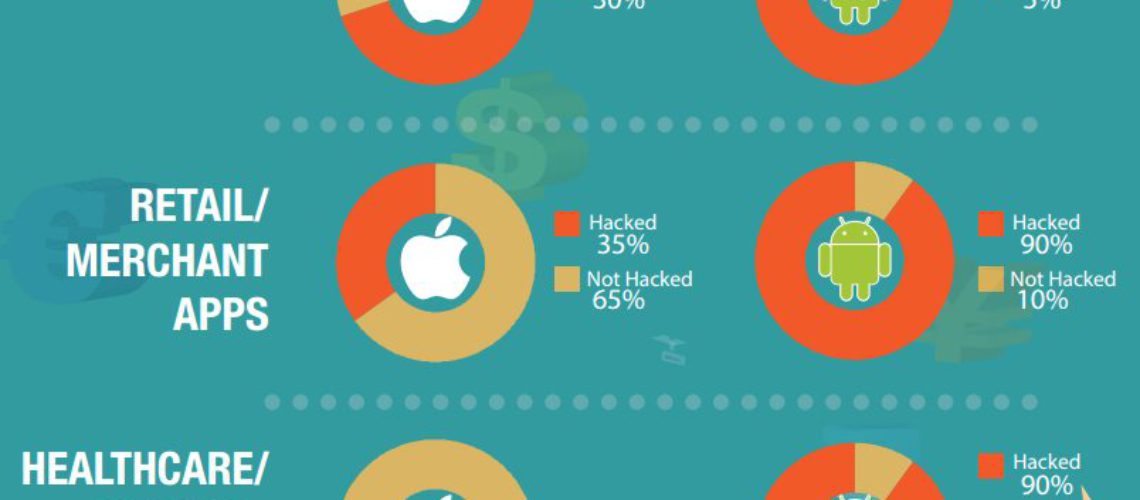
The research showed that the Android apps got most of the cybercriminals attention. In other words Android apps had the lead with cloning rate of 80 %, followed by iOS apps with cloning rate of 75 %. The results were estimated on multiple dimensions: health care, financial service and retail. The top apps in each category were studied and the result showed that the apps that are most cloned were:
- Android apps: 95% – financial, 90% – healthcare, and 90 % – retail business.
- iOS apps: 35 % – merchant, and 70 % – financial-related software recorded, 0 % healthcare.
These three main app types are expected to keep the interest of the cybercriminals, as they all deal with the exchange of information that is sensitive, both personal and financial. The research made it clear that the companies and the users that apply the different apps should be very careful and security aware, taking the necessary precautions.
According to the different reports, the mobile applications show vulnerability to reverse-engineering, repackaging, republishing. One way in which the data protection on iOS and Android devices can be done by the users themselves is by keeping the original defenses provided by the manufacturer. Another way is never to download and install software that is coming from untrusted sources. The companies should also take measures into protecting their products.