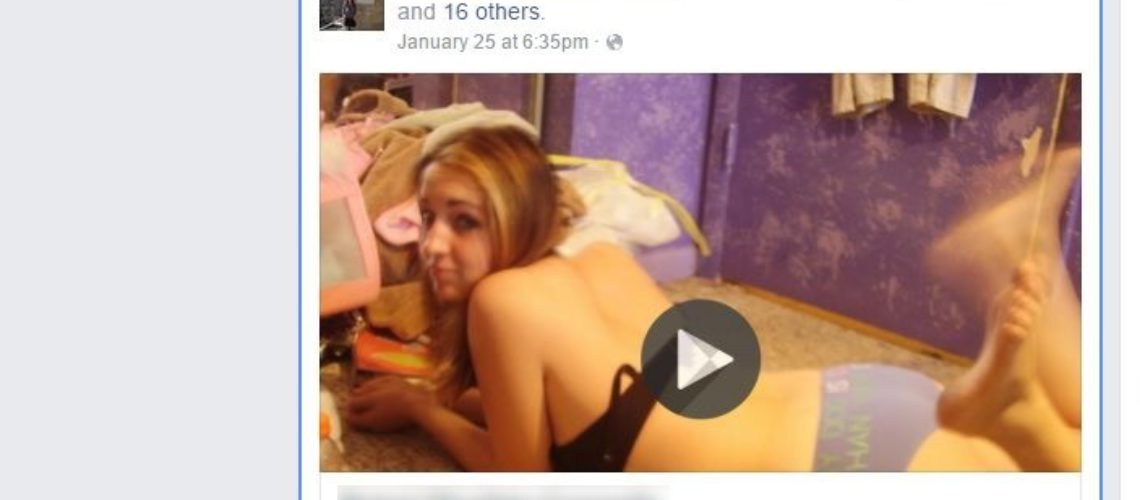
Last week a new Trojan circulated on Facebook, infecting more than 110 000 users of the social network in just a couple of days. The Trojan spread by tagging friends of the victim in a special post containing a lure video. According to the researchers the tag scams are not new, however their usage has increased recently.
Aggressive Trojan Distribution
The producer of the antivirus programs Bitdefender, a company based in Romania, has published an analysis last week of the scam during which more than 20 people from the friends’ list of the victim are tagged in a malicious post which is trying to lure other victims. The attack a few days ago was so aggressive that for less than an hour the number of victims increased to more than 5000 Facebook users.
When clicking on the message, the user is taken to a page wherefrom to see a preview of an adult video. That video is interrupted just after a few seconds and the viewer is offered to download a malicious file pretending to be a Flash Player update, to see the rest of the video material. At that moment the download process starts automatically.
Other similar scans have also been discovered and thus the number of the victims is increasing. The cybercriminals responsible for the Trojan attacks rely on an aggressive distribution method, 名前付き “Magnet” by the researchers. This method allows friends of the victim’s friends to see the post and click on the malicious link.
That is a new practice as in the previous cases the victim would send the lure to other friends and only the infected ones would offer it to their contacts.
Cybercriminals from Turkey
When the researchers inspected the malware, their analysis showed that the Flash Player fake update resembles a set of executable files found on the system that is compromised. These files are from the types wget.exe, chromium.exe, verclsid.exe, arsiv.exe.
The expert Mohammad Reza Faghani says that the Trojan gains control over the keyboard and the mouse. The threat will be further inspected, so that the full damage of the malware can be revealed and known for. On the bright side, currently many of the antivirus programs were able to detect the Trojan and to prevent its activity.
The malware expert Mohammad Reza Faghani confirmed that two of the domains that are contacted by the Trojan were registered three months ago, in October 2014. The IP of one of the domains (filmver[.]com) points to the Cloudflare network, while the IP for the other (pornokan[.]com is based on a server positioned in Amsterdam. Both domains are registered by the Turkish company FBS INC that provides domain names registration services.
Another domain (videooizleyin[.]com) was also found to host the malicious videos and it is also associated with the network Cloudflare. That domain in particular has been registered several days ago, which means that the cybercriminals are active.
According to the analysis of the scam with the Trojan, Bitdefender has found out that the cybercriminals are from Turkey, を使用して “schwarzback” as the online alias. It seems that the tag scams reports come from one group that is using multiple registrars and domains.