New spam has been attacking the computers these days, tricking the users into believing that they get Chrome web browser update, while actually they receive the file-encryption malware Critroni. The users get a message that this update is due and that it is accessible at the online location that is stated in the message. The cybercriminals then set up a redirection mechanism that is very dynamic.
A ransomware threat, Critroni is a CTB-Locker that encrypts the data found on the system that it affects and then asks for a fee to unlock the files that are kept.
Chrome Installers Possible from Numerous Locations
The Malwarebytes expert Jerome Segura confirmed that the malicious threat is downloaded from websites that have been altered by the cybercriminals in order to host the malicious piece. The threat is received through a dynamic redirection mechanism known as assetdigitalmarketing[.]com/redirect[.]php. The victim of the attack receives a file that pretends to be a Google Chrome installer. When this malicious file is launched, it starts an encryption process and then then a ransom message is released as the operation is completed.
Users can actually retrieve data without paying the ransom in case it is one of the older variants of the malware. This however does not delete the shadow copies of the files that were created by the Windows Volume Shadow Service. The files can also be recovered by applying programs such as Shadow Explorer.
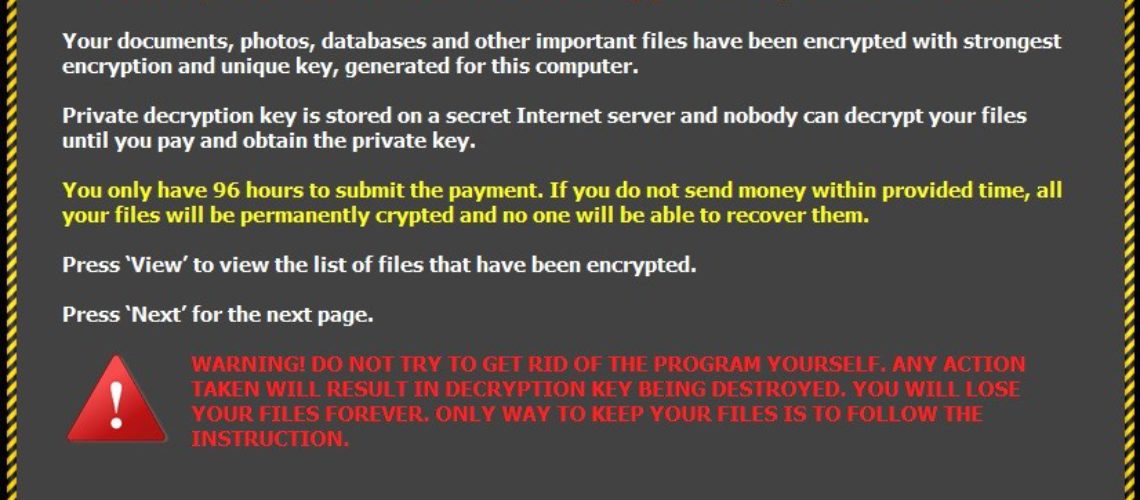
The new CTB-Locker is more expensive
The new versions of Critroni features an extended grace period (96 hours versus 72 hours before that) in which the victims can make the bitcoin payment. しかしながら, there is also a change in the financial demands. In the newer versions, Critroni is asking for a few hundred dollars opposed to the sum of less than 50 USD it demanded in the summer of 2014. The new Critroni version ransom message further comes in many languages as well and further offers the option for decryption of five items in good faith.
The experts have checked the newest version of Critroni ransomware, known as Trojan.ZBAgent.NS, which givesn deadline of 96 hours and requests a payment of 2 ビットコイン (approximately 450 USD or around 400 Euros). In case no payment is made and the 96 hours are over, then the key needed to decrypt the data is deleted from the server and the files of the victim remain encrypted.
What Should the User Know
Users should be aware that the Google Chrome activates automatically in the background of the system and does not require intervention from the user. This is a seamless process where the new version becomes available when the application is re-launched by the user.
Mozilla Firefox uses own automated update process and Internet Explorer gets the latest updates through Windows Update. The new program versions are never delivered through email and usually there are in-program alerts in case such versions are released.