The Razy virus has been released in an updated variant which also uses AES encryption cipher to encode the files of the computers it encrypts. After this has been done, the ransomware drops a ransom note where it asks 0.5 BTC from the user as a ransom fee, promising to decrypt the files after payment. Many users who have been infected by this virus report that it uses it’s distinctive .razy1337 file extension which it adds to the encrypted files as a suffux after the encryption.
More Information about Razy Ransomware
Upon infection the ransomware may create several files on the computer of the user, such as executable files in .exe file format, files that can be opened with Windows Command Prompt, like .bat or .cmd and files that are system and support files for it’s main executable, like .tmp, .dll or other similar.
The files dropped by the new Razy ransomware may exist in several key folders of Windows, primarily in:
- %SystemDrive%
- %User’s Profile%
- %Temp%
- %System32%
- %LocalRow%
- %Roaming%
- %Local%
After the files are dropped, the new Razy ransmware version may begin to employ encryption on the files of the infected computer. It looks for videos, music, databases, pictures, documents and other files that may be associated with programs that are often used on the computer.
After having encrypted the files of the user, Razy begins to employ a very specific encryption algorithm, called Advanced Encryption Standard which alters segments of the code of the files, making them no longer openable. The files may look like the following:
- {Filename}.{File Extension}.razy1337
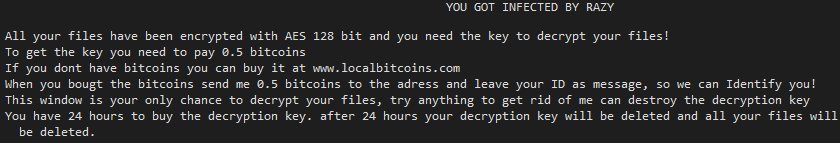
After this, Razy changes the wallpaper of the user and also drops it’s ransom note to notify the user of what has happened:
Razy ransomware may be also rather specific when it comes to defense as well. The ransomware may shut down in case it is ran on a virtual drive instead of on a real Windows. This is done to prevent researchers from tracking it’s activity and to which servers it communicates.
How Did I Get Infected With Razy’s New Version
As soon as the ransomware begins to spread, users immediately start to become infected, primarily because it is undetectable yet. This is done by using the so-called program obfuscators which make it possible to avoid firewalls and real time shields. These are combined with either malicious script in web links or with a file that may be sent via e-mail as an attachment, for example. As soon as an inexperienced user believes the fake e-mail that is sent is real and opens the attachment, the infection is already conducted.
How to Remove Razy Ransomware and Try To Get My Files Back
In case you have become an unfortunate victim of Razy’s new version, we advise you to focus on going for the immediate removal of this malware from your computer, after which look for methods to reverse your files. Direct decryption is not possible at the moment, but there is a variety of other tools you can use that can help you restore your files:
Data Recovery Software.
Network Sniffers.
Backups you have created.
Other decryptors by Kaspersky or Emsisoft.