This post is created to help you detect if the legitimate page Trojan.Win32.SEPEH.gen is imitated by a real malware that might be infecting your PC and remove it permanently so that your computer is safe.
Computer Trojans are the ultimate form of spyware out there which aims to also remotely control your computer system from distance. And the Zeus Trojan is no exception from this rule. It can remain undetected on your computer system for a very long time, while being disguised as a legitimate program. If your computer shows any signs of having the Trojan.Win32.SEPEH.gen imitated by a malware or other threats, we strongly suggest that you read this post to learn more about it and how to protect your computer immediately and in the future too.
| Threat Name | |
| Category | A legitimate site, but could also be imitated by malware.. |
| Main Activity | Slithers onto your computer and heavily modifies your web browser settings to cause advertisements and collect data. Mostly displays browser redirects to pages. They may ask you to accept Push Notifications or enter personal information. |
| Signs of Presence | Multiple third-party advertisements as well as a slow down in computer performance. |
| Spread | Via software bundling or by getting you to download and run it. |
| Detection+Removal | DOWNLOAD REMOVAL TOOL FOR |
How Does Work
was created by developers who also are a brand of the some of the most famous PUA(Potentially Unwanted Application) maker groups. The ad-supported character of this software makes it to often be categorised by users as adware, which is not far from the truth. However, because the application is not malicious and is also classified as a low-level type of threat many antivirus programs tend to skip it.If it is active on your computer, some of the signs to notice it are:
- Seeing “Ads by ” or “A Ad” or any similarly caption advertisements showing as pop-ups, banners, etc.
- Noticing phishing web pages or browser redirects to third-party search engines, besides the original one used by default on your web browser.
- Sluggish performance of your computer.
In addition to this general activity of , the add-supported program may also perform multiple different types of advertisements that link to various third-party websites. And this is not good, because those programs may collect certain specific information from your computer using:
- Pixels.
- Flash cookies.
- Tags.
- Web cookies.
- Others.
Such technology can be used to obtain your:
- IP address.
- Search history.
- Mouse clicking history.
- Tracking of your search history.
- Browser history.
This data may then be used to display targeted advertisements or for other purposes that have nothing to do with your interest. Some third-party websites which may be linked either via or it’s advertised entities, may redirect you to a malicious web link that may prompt you to download a fake installer or a malicious web link. Such malicious objects can even infect your computer with different malware:
- Ransomware.
- Worms.
- Trojans.
- DDoS software.
- BitCoin miners.
- Banking malware.
- Keyloggers.
What Does Redirect Do on My Computer?
Adware or ad-supported software is a category of programs which are created to show different types of advertised content on your computer system. This content includes displaying pop-ups, redirecting tabs from your web browser to web pages that are unfamiliar and may cause your PC harm.
Other side effects of having adware programs such as on your computer is that the software begins to collect your data without your approval. Usually most adware programs do not notify that they collect data and these software are often deemed to be malicious.
How Bad Does Adware Affect You?
Besides it’s primary goal – do show you various types of adverts and collect your information, _ adware does not aim to show you that it’s there. There may usually be several signs that the program is installed on your computer and these signs may be the:
- Name of the program on the displayed advertisements.
- installed as a suspicious browser extension, that pretends to be legitimate.
- If it is situated on your Windows Programs and Features.
Since detection of the Adware program can be a tricky process, because most of the files it creates are concealed in different Windows locations, removal of it may be a tricky process. You can try to locate it’s suspicious web browser extensions on your Chrome, Firefox, Explorer or other browser and you can try to uninstall it from the Programs and Features menu in Windows. However, this does not guarantee that the program won’t be back after this, like it usually happens with such software. This is the main reason why an adware-specific removal program should be used to scan for and delete all of the objects related to browser hijacker from your computer system.
Removal Instructions for
If you want to remove , we strongly recommend that you first backup your data, just in case something goes wrong. Then, you can follow the manual or automatic removal instructions below, depending on which type of steps suits you more. If you lack the experience and the confidence that you will remove manually, then you should do what most experts would and save yourself some time by downloading and running a scan with an advanced anti-malware software. Such programs are created to quickly identify and remove threats and programs with intrusive behaviour, like , plus they also aim to ensure that your system is protected against future intrusions as well.
Preparation before removal of :
1.Make sure to backup your files.
2.Make sure to have this instructions page always open so that you can follow the steps.
3.Be patient as the removal may take some time.
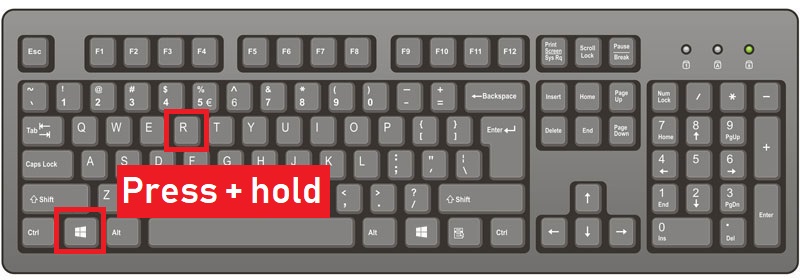
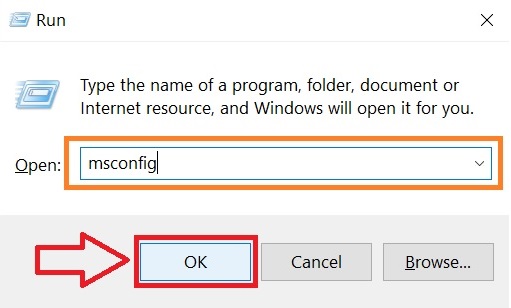
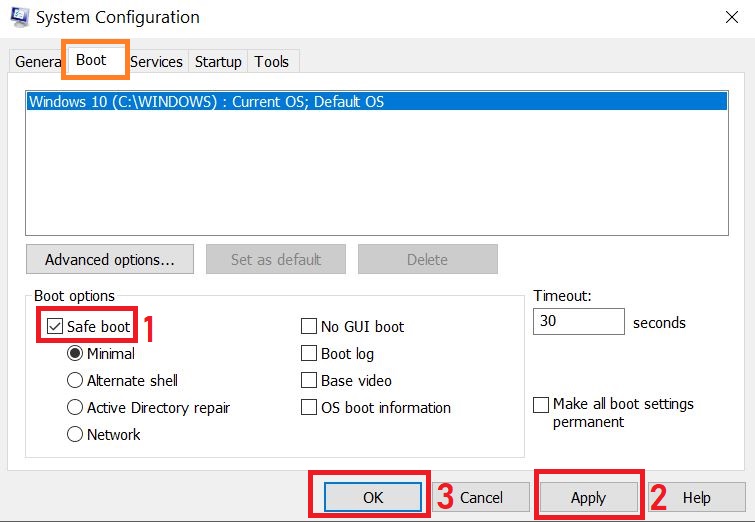
Step 1: Reboot your computer in Safe Mode:
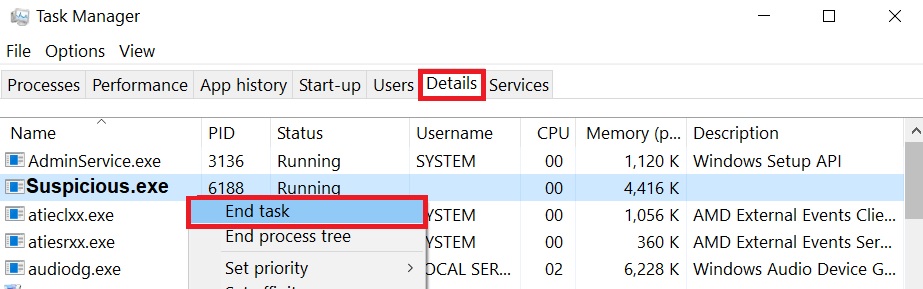
Step 2: Cut out in Task Manager
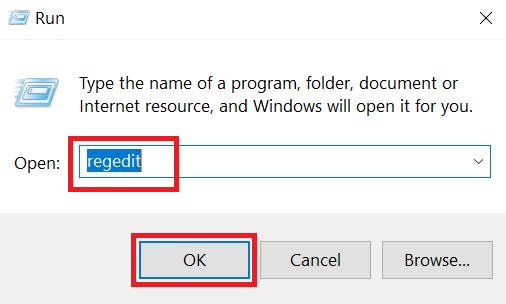
Step 3: Eliminate ‘s Malicious Registries.
For most Windows variants:
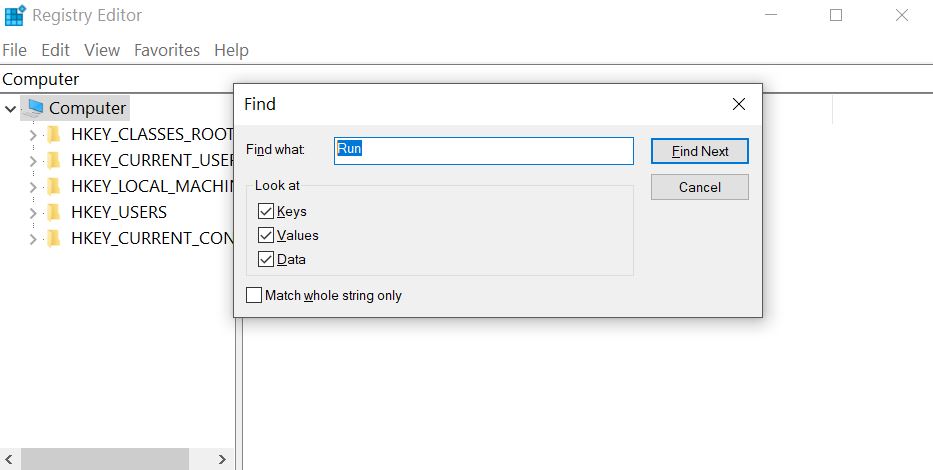
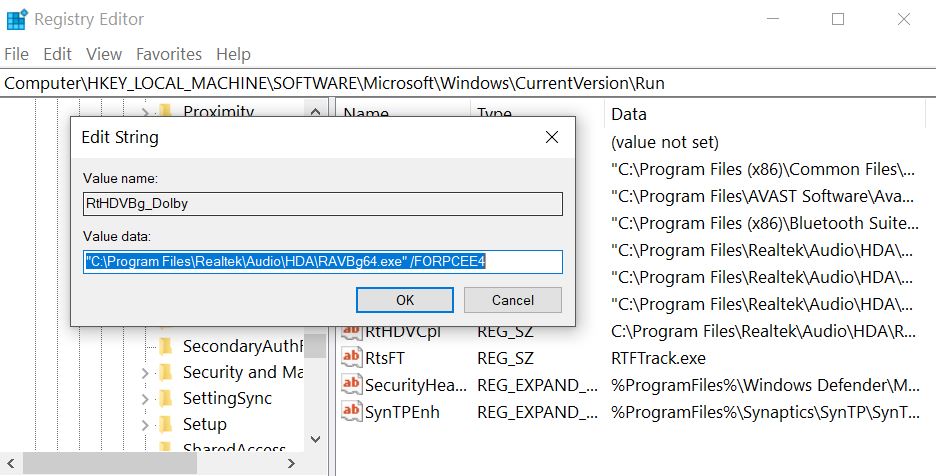
Step 4: Scan for all virus files, related to and secure your system.
If you are in Safe Mode, boot back into normal mode and follow the steps below
It is advisable to run a free scan before committing to the full version. You should make sure that the malware is detected by SpyHunter first.