What Is the Trojan Detection?
Trojan is a potentially unwanted program (PUP). This is a type of software that is not necessarily malicious, but may have undesirable and potentially dangerous effects on your computer. Trojan is ad-supported and could also act as a browser hijacker by changing your browser’s settings without your your knowledge or consent. These programs can be intrusive and can slow down computer performance, display unwanted advertisements, or redirect you to malicious websites. Additionally, PUPs such as Trojan can compromise your online security or personal information.What Does Trojan Do?
Trojan is a suspicious site and application mainly used to capture personal information from users for advertising revenue.It is compatible with the most commonly used browsers like Internet Explorer, Google Chrome and Mozilla Firefox. Upon installation, it is likely that it will alter your browser’s settings and change your default home page to its own.
Trojan may cause redirects to suspicious and scamming pages. Interacting with any of the content Trojan provides is not advisable, as it may expose you at various risks.Once installed, Trojan may start displaying advertisements and sponsored links in your search results, and may disturb your browsing habits. And, by clicking on any of those ads, you expose your PC at risk again.
The worst part about this browser hijacker is that it uses tracking technology to monitor your browsing behavior and record that information along with other personal information, such as usernames, emails, etc. This data may then be sold to third parties, such as advertising agencies, aiming to improve their targeting and display custom ads in accordance with your searches.
| Threat Detection | Trojan |
| Type | Browser Redirect Alerts |
| Detection+Removal | Download SpyHunter (FREE Trial!)*
|
How Did Trojan Enter Your PC?
In most cases, unwanted software such as Trojan enters your PC bundled with freeware you download. That is why you must always pay attention when installing any software. Bundled software usually is mentioned in the installation process, and you are given the option to opt out of it.
Note that bundling is a popular method used by the creators of adware and malicious software because they are aware that users rarely read everything during the installation. Adware developers intentionally create “recommended” installation settings. Therefore, in order to be safe, simply disallow the recommended settings and choose the “advanced” or “custom” option instead.
How to Remove Trojan?
In case you already have the Trojan detection on your computer, don’t worry as there is an easy way to remove it. Follow the instructions below to install a trustworthy anti-malware program that will take care of the removal process for you. Manual instructions are also provided for tech-savvy users.
Preparation before removal of Trojan:
1.Make sure to backup your files.
2.Make sure to have this instructions page always open so that you can follow the steps.
3.Be patient as the removal may take some time.
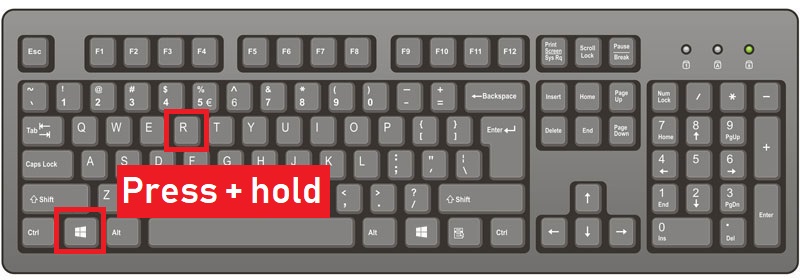
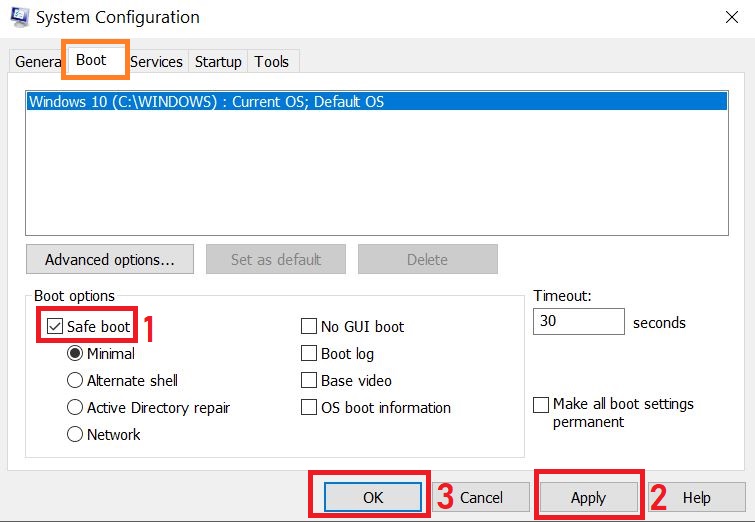
Step 1: Reboot your computer in Safe Mode:
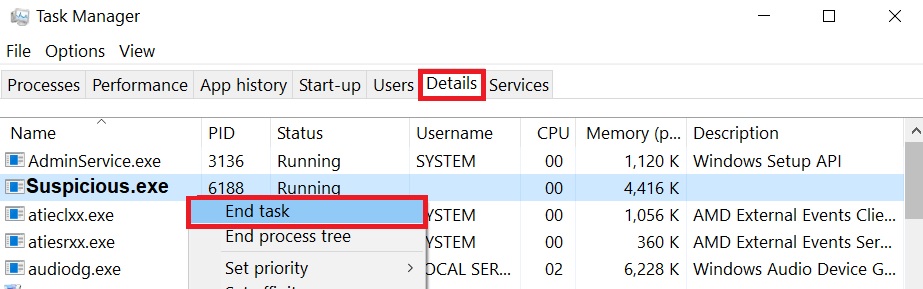
Step 2: Cut out Trojan in Task Manager
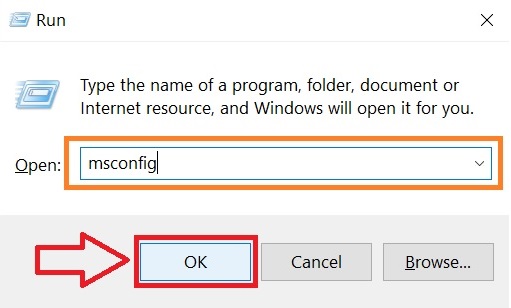
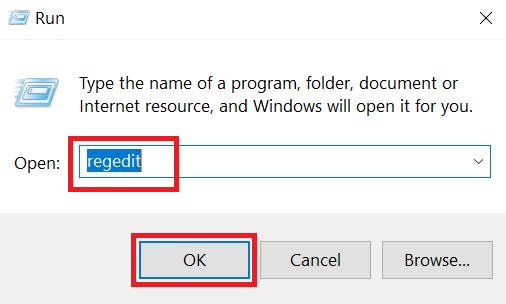
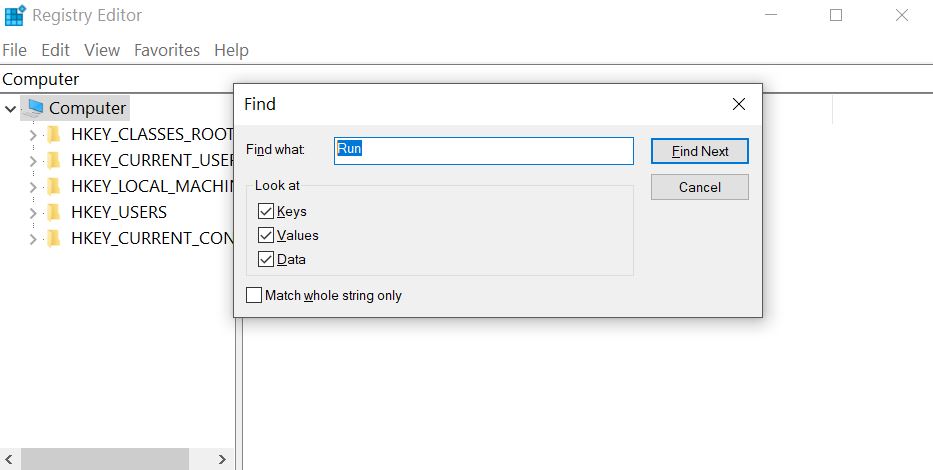
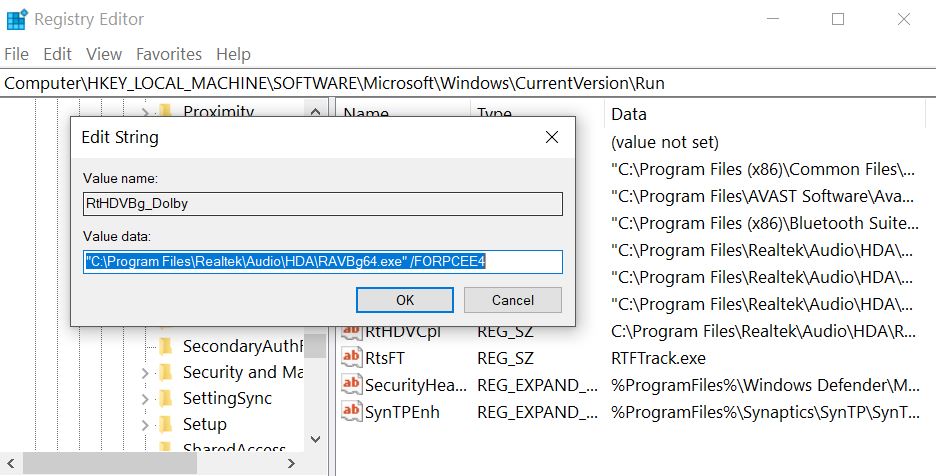
Step 3: Eliminate Trojan‘s Malicious Registries.
For most Windows variants:
Step 4: Scan for all virus files, related to Trojan and secure your system.
If you are in Safe Mode, boot back into normal mode and follow the steps below
It is advisable to run a free scan before committing to the full version. You should make sure that the malware is detected by SpyHunter first.