Crysis ransomware virus is a new cyber threat that has emerged in March this year, and although it has been quiet for awhile, it has erupted again. The most distinctive feature of Crysis is that it adds .crySIS extension to the files it encrypts. No decryption key has been created for this virus yet, so if your PC has been attacked by it, chances are you have lost your files for good. Paying the ransom, しかしながら, is not an option as the virus will remain inside your system and may strike again. また, you may never receive a decryption key even after you pay the cyber criminals. Best thing you can do then is to remove Crysis as soon as possible and only after that you may try to restore some of your files with a file recovery tool.
How Does Crysis Ransomware Enter Your PC
Crysis sneaks into your PC just like most ransomware viruses do – via corrupted email attachments and embedded links. Once the attachment or URL is opened, the infection begins. File sharing networks, しかしながら, are also used to deliver this threat.
Be extra careful when opening emails with an unknown or suspicious sender. Keep in mind, that ransomware developers are very creative when it comes to creating the email carrier of their viruses. They may use email sender names of institutions, organizations, companies, people, websites, 等. that you are likely to use or be familiar with, and this way you can easily be tricked to open the corrupted email.
How Does Crysis Ransomware Work?
Crysis uses the RSA encryption algorithm and the AES-128 encryption to encrypt targeted files. Once it’s activated on the victim’s computer, it scans it to detect the following files for encryption:
.エピソード, .odm, .応答, .ods, .odt, .docm, .docx, .doc, .odb, .mp4, sql, .7と, .m4a, .rar, .wma, .gdb, .税金, .pkpass, .bc6, .bc7, .avi, .wmv, .csv, .d3dbsp, .zip, .君は, .和, .ibank, .t13, .t12, .qdf, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .ゴー, .場合, .svg, .地図, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .メニュー, .レイアウト, .dmp, .ブロブ, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .リム, .w3x, .fsh, .ntl, .arch00, .レベル, .snx, .cf., .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .バー, .upk, .インクルード, .私は、Wi, .litemod, .資産, .フォージ, .ltx, .できる, .apk, .re4, .sav, .lbf, .こんにちは, .ビック, .epk, .rgss3a, .その後, .大きい, 財布, .wotreplay, .xxx, .説明, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .ペム, .crt, .cer, .の, .x3f, .srw, .ペフ, .ptx, .r3d, .rw2, .rwl, .生, .raf, .orf, .nrw, .町, .mef, .erf, .kdc, .dcr, .cr2, .crw, .ベイ, .sr2, .srf, .arw, .3fr, .沿って, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .PST, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps.
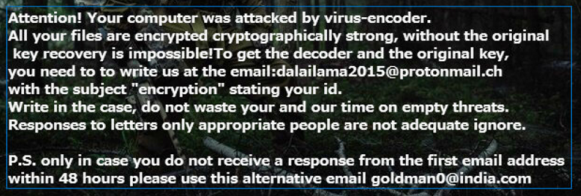
Once the files are scrambled, Crysis ransomware drops 2 text files with instructions on how to pay the ransom in exchange for a decryption key in the directories where it has encrypted the files. The ransom message looks like this:
…and it reads like this:
注意! Your computer was attacked by virus-encoder.
All your files are encrypted cryptographically strong, without the original key recover is impossible! To get the decoder and the original key, you need to to write us at the email:[email protected] with subject “encryption” stating your id.
Write in the case, do not waste your and our time on empty threats.
Responses to letters only appropriate people are not adequate ignore.
P.S. only in case you do not receive a response from the first email address within 48 hours please use this alternative email [email protected].
This message also replaces the victim’s desktop image, so it won’t be skipped or missed out.
加えて, notice the 2 email addresses in the ransom message above – one belongs to a domain in the Czech Republic, and the other – to a domain in India.
これまでのところ, しかしながら, the origin of Crysis ransomware is unknown.
How to Remove Crysis Ransomware from Your PC
As said earlier, paying the ransom fee to the cyber crooks is not advised as this way you only encourage the virus developers to continue spreading such infections. The best way to stay protected from any type of online threat is to prevent it from entering your PC. And you do that via strong anti-malware protection that could be a combination of an anti-virus and a second-generation anti-malware tool. また, make sure you always back up your files and have them on an external hard-drive. こちらです, even if you get attacked by a ransomware infection, you could easily deal with it.
In case you haven’t done any of the above, and your files are already containg the .crysis extension in their names and are inaccessible, you need to remove the Crysis ransomware immediately first. そして, you can do that by a strong anti-malware tool that will scan your system, detect the malicious components and remove them safely and efficiently.