The Magnitude Exploit Kit also dubbed Popads has been around for quite some time. It has been used by Cutwail cyber criminals to substitute the BlackHole EK. A while back, the Magnitude EK was spread across the Web via malicious spam Pinterest emails. Basically, it was employed to install the ZeroAccess rootkit as well as the Zbot/Zeus Trojan. To attack users’ computers, the EK leveraged a number of vulnerabilities, combined with the good old social engineering schemes.
As reported by the security researcher Kafeine, the Magnitude EK is back, this time exploiting a zero-day Adobe Flash vulnerability – CVE-2015-3113 that has been unveiled recently. The vicious EK has been on the verge of Flash 18.0.0.160 on Internet Explorer 11 in Windows 7. Interestingly enough, the attack was detected only four days after the vulnerability was patched by the Adobe theme.
The Malicious Combo – Magnitude EK ft Cryptowall
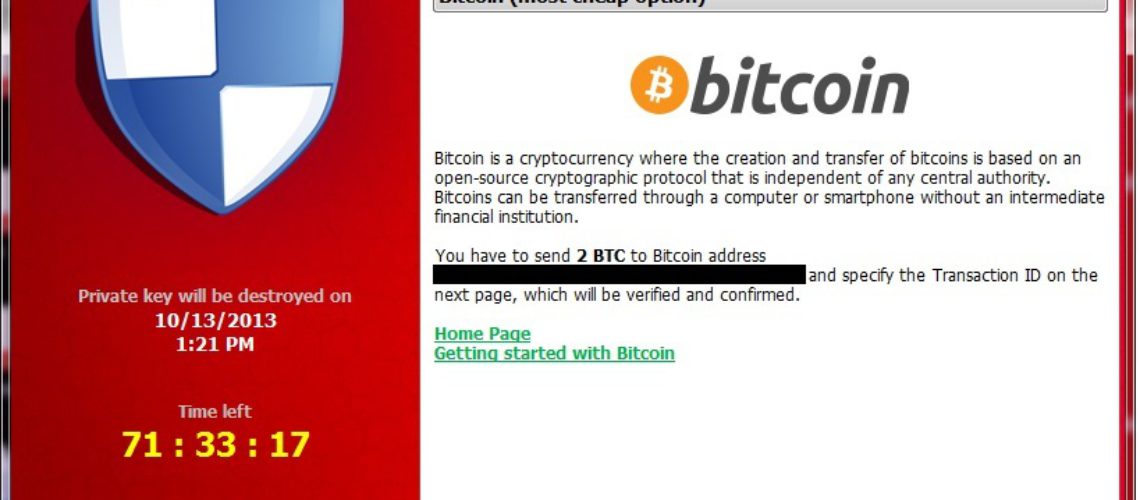
As a result of the vulnerability’s exploitation, the Magnitude EK has been spreading the infamous Cryptowall. As reported by the FBI, the Cryptowall ransomware has generated over $18 million in about a year. The ‘profit’ cyber criminals have gathered solely comes from user expenses.
Once installed on a victim’s computer, the Cryptowall ransomware demands an average fee of about $500. The fee should be paid within a given deadline, or the user’s encrypted files will not be decrypted. しかしながら, security researchers always highlight the fact that paying the ransom doesn’t necessarily mean data decryption will happen. As visible from the huge number stated by the FBI, ransomware is designed to generate revenue for its creators and should not be trusted. また, remember that the best precaution against encrypting cyber threats is data backup.
Let’s go back to the Magnitude EK and its connection to Cryptowall. According to research, on June 26 about 95 percent of users around the globe have some version of Adobe Flash currently installed. At least 55% percent of them use an unpatched version of Flash making their machines vulnerable to various malicious attacks.
Immediately Update or Completely Uninstall Adobe Flash Player
Considering the high percentage of unpatched Adobe Flash users, it is easy to see why cyber crooks love to exploit such vulnerabilities. In case you are one of the users that are currently running an unsafe Flash player, patching it immediately is high advisable. Adobe Flash Player on Google Chrome and Internet Explorer will update automatically. しかしながら, standalone installations will not be updated unless you have set them up to do so.
If you are not a keen Adobe Flash user or simply don’t need it, uninstalling it completely may be a good choice. Widely used browsers are equipped with a click-to-play feature that can substitute the often leveraged Adobe product.