 Yet another version of the Cerber Ransomware has been released out into the wild web to wreak havoc for profit. The ransomware virus uses advanced techniques to encrypt the data on the computers which it infects after which ask for 499$ for ransom payoff. The Cerber ransowmare’s 4.1.6 version also uses several different improvements, primarily when it comes to it’s infection and distribution which is massive. Anyone who has been infected by this Cerber version is advised to read this article and remove the ransomware as well as try some alternative methods to restore their files.
Yet another version of the Cerber Ransomware has been released out into the wild web to wreak havoc for profit. The ransomware virus uses advanced techniques to encrypt the data on the computers which it infects after which ask for 499$ for ransom payoff. The Cerber ransowmare’s 4.1.6 version also uses several different improvements, primarily when it comes to it’s infection and distribution which is massive. Anyone who has been infected by this Cerber version is advised to read this article and remove the ransomware as well as try some alternative methods to restore their files.
More About Cerber Ransomware 4.1.6
When it comes to the Cerber ransomware viruses one thing is clear – they are managed by a lot of affiliates all over the world, which means that you can get infected by a lot of methods:
- E-mail phishing
- Posted as a fake program on torrent websites.
- Uploaded on an archive in suspicious sites.
- Malvertised on a malicious site or via an unwanted program that displays advertisements and browser redirects.
- Dropped from a malicious web link containing JavaScript or other forms of malicious coding.
After having done this, サーバー 4.1.6 ransomware may drop several malicious files on the compromised computer, primarily in the key Windows folders which are:
- %System%
- %システム32%
- %アプリデータ%
- %一時%
- %ユーザーのプロファイル%
After Cerber ransomware has dropped the malicious files, the virus begins to perform activities that may close several processes on the compromised computer, like the database running process. This is because the newer versions of Cerber (4.1.5 そして 4.1.6) now are more focused on encrypting whole databases, for example Microsoft Access, Oracle and MySQL database files.
After being installed on the infected computer, the infection module which is usually the RIG exploit kit’s latest Empire Pack version, uses an obfuscated command in PowerShell to download the encryption modules of Cerber.
After these files are downloaded, the Cerber 4.1.6 ransomware begins to heavily modify the registry entries so that it is comfortable for it’s encryption modules to run every time Windows boots. The Run as well as the RunOnce registry keys may be affected by this. These subkeys are located in the following keys:
→ HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\
After this the ransomware may begin the encryption process and render all of the files with changed names and completely random file extensions.
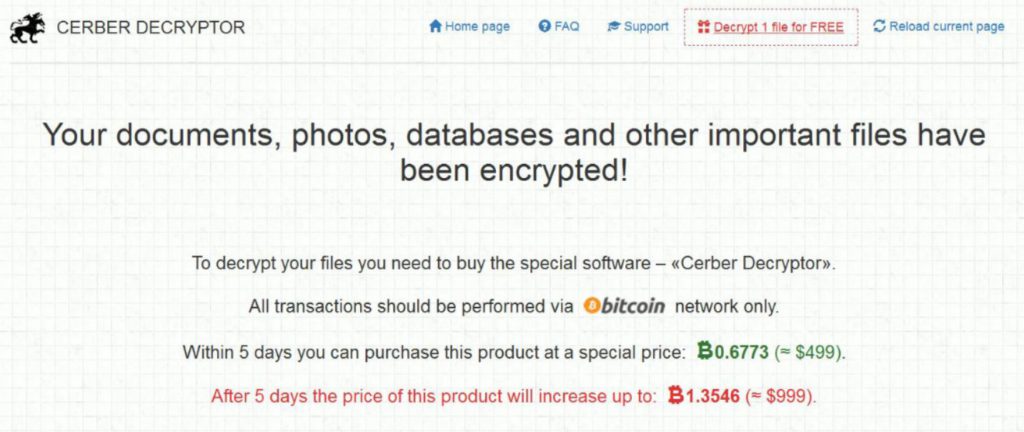
The wallpaper has a web link which when visited via the Tor network, displays a screen with the following ransom note:
“How to get «Cerber Decryptor»?
1. Create a Bitcoin Wallet (we recommend Blockchain.info)
2. Buy necessary amount of Bitcoins
Do not forget about the transaction commission in the Bitcoin network (≈ 0.0005).
Here are our recommendations:
btcdirect.eu – A good service for Europe
bittylicious.com – Get BTC via Visa / MC or SEPA (EU) bank transfer
localbitcoins.com – This service allows you to search for people that want to sell Bitcoins directly (WU, Cash, SEPA, Paypal, 等).
cex.io – Buy Bitcoins using Visa / Mastercard or Wire Transfer.
coincafe.com – It is recommended for the fast and easy service. Payment methods: Western Union, Bank of America, cash through FedEx, Moneygram, and/or wire transfer
bitstamp.net – Old and proven Bitcoin dealer
coinmama.com – Visa/Mastercard
btc-e.com – Bitcoins dealer (Visa/Mastercard, 等)
Could not find Bitcoins in your region? Try searching here:
buybitcoinworldwide.com International catalog of Bitcoins exchanges
bitcoin-net.com – Another Bitcoins sellers catalog
howtobuybitcoins.info – International catalog of Bitcoins exchanges
bittybot.co/eu – A catalog for the European Union
3. Send (499$) to the following Bitcoin address:」
For the encryption, this iteration of Cerber ransomware uses the strong combination of the AES and RSA file extensions to cause an encryption. This makes every file unique and a unique decryption key corresponding to it. It also makes it very difficult for malware researchers to decrypt the files.
Remove Cerber 4.1.6 Ransowmare and Try to Get the Files Back
Security experts strongly advise against using the instructions to pay the ransom, because you collaborate with criminals and trusting criminals is always a bad decision.
Instead it is strongly recommended to remove the 4.1.6 Cerber variant using an advanced anti-malware tool for best results, after which attempt one of the following methods to revert your files back to normal:
- Data recovery tools.
- Shadow Volume Copies software, like Shadow Explorer.
- Network sniffer while still infected to analyze the communication with the servers of Cerber.
- Try third-party decryptors. To do this you can see Kaspersky, Emsisoft, TrendMicro and Eset’s decryptors, but it is strongly advisable to decrypt 1 file for free on the Cerber’s web page first and then backup all the files somewhere else because they may break when you try third-party tools to decrypt them.
