A new version of Petya ransomware has surfaced out into the open after it’s younger sister – Mischa ransomware. The ransomware uses sophisticated encryption to encode hard drives, similar to it’s previous version. Many feel convinced that this is an improved version of the viruses since they were successfully decoded via a decryptor, named Petya Sector Extractor which was later discontinued. In case you have become a victim of GoldenEye ransomware, you should know that it encrypts your drive to demand the sum of 1.36 BTC as a ransom to decrypt it. Since the ransomware was previously decrypted, we urge you to read our information about it and instead of paying the ransom try alternative methods to restore the encrypted files by GoldenEye.
More Information about GoldenEye Ransomware
Just like it’s other ransomware variants, GoldenEye also uses encryption on the MBR(Master Boot Record) to render the hard or solid state drives no longer useful. But to infect users first, the malware uses sophisticated techniques. One of them is to combine several exploit kits, JavaScript tools as well as obfuscators that conceal the malware from several different real-time shields of antivirus programs. These all may be combined in a malicious macros or scripts that may replicate as the following e-mail attachments:
- .js or .wsf JavaScript files.
- Malicious Microsoft Office or Adobe Macros (.docx, .pdf, .xts, pptx, etc.)
These may be contained in an archive, for example .zip or .rar files that may be sent to the user via fake e-mails, for example:
Dear Customer,
Greetings from Amazon.com,
We are writing to let you know that the following item has been sent using Royal Mail.
For more information about delivery estimates and any open orders, please visit: {malicious web link} or {malicious attachment}
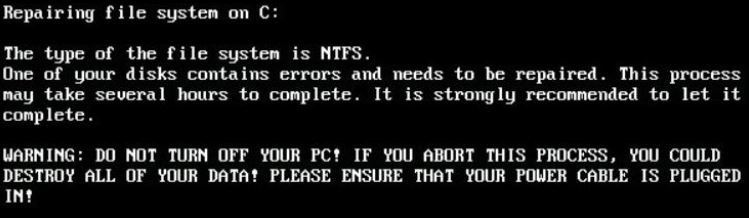
Once the user clicks this e-mail, GoldenEye ransomware begins infecting his computer. It may immediately set registry entries to make the virus run on system boot. After this, GoldenEye ransomware may restart the computer of the victim, displaying the following fake screen:
What the virus actually does during the displaying of this screen is to begin encrypt the hard drive. After it’s encryption is complete, GoldenEye ransomware displays the following screen:
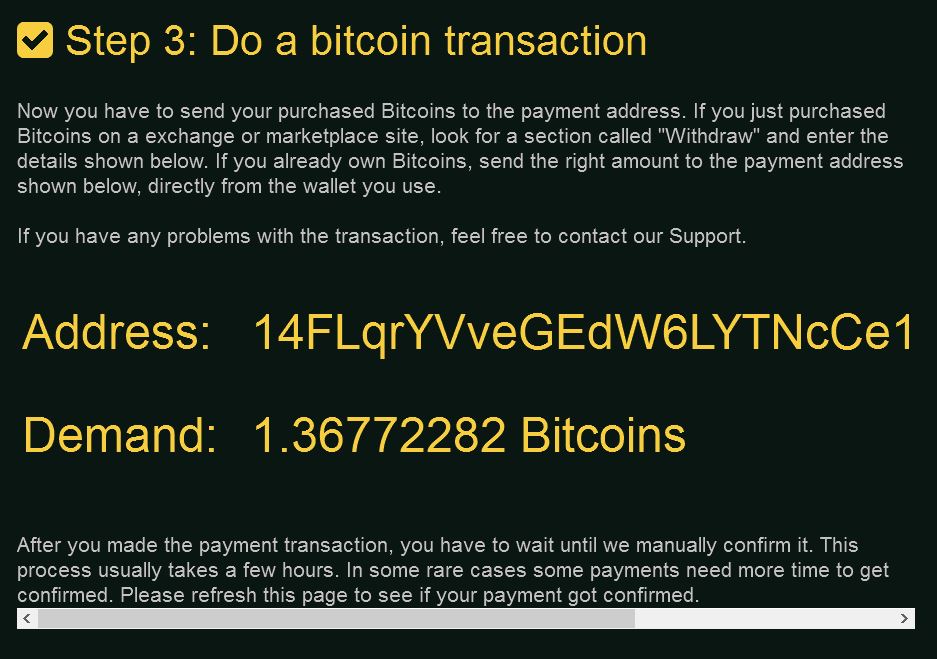
After pressing any key, the user is presented to a locked screen which has instructions on how to pay a hefty ransom fee via a web page:
The web page, typically to most ransomware viruses is also Tor-based and has detailed steps on paying the ransom and even CAPTCHA identifier:
GoldenEye Ransowmare – Conclusion, Removal and Decryption Scenario
In order to deal with GoldenEye ransomware, a very specific approach should be considered. Experts strongly advise to perform the followingactions:
1. Remove the drive from the infected laptop.
2. Secure another computer with an advanced anti-malware program.
3. Insert the infected drive into the other device.
4.Download the Petya Sector Extractor to find a decryption key corresponding to your particular infection.