The Duqu 2.0 also known as Win32.Duqu.B is classified as a collection of different malware discovered by security researchers from the Budapest University of Technology and Economics. It is a powerful set of malware tools, but primarily a Trojan RAT that does not replicate and works through exploits. The 2.0 version contains no actual code in the industrial control system and it has intelligence gathering modules targeted at communication devices that may belong to different telecommunication providing companies.
What Is Duqu 2?
According to Symantec’s report on Duqu, it is mainly a Trojan Horse, that may assume control over a system and gather information without being detected for long periods of time but also it includes other extensive features. The malware is mainly targeting particular organisations with the purpose of gathering targeted information. However, the report also states that it is possible for other organisations to become victims of the software. When Symantec experts examined its source code, they concluded that the creators of Duqu could have had access to a previous malware, called Stuxnet (W32.Stuxnet)`s source code and then possibly modified it for specific purposes.
How Does Duqu 2.0 Operate?
To run, spyware needs to infect the system first. This virus is believed to have an encrypted installer executable that in some cases is thought to be deployed on the system initially. After that the actual attack may begin as a DLL, containing embedded files, configuration file and a driver file are installed and registered by the executable file that plays the injector role. The DLL file is injected into the Windows process services.exe (for Windows PCs) and after that the DLL starts the same injecting procedure to other processes which may mask the program`s activities and bypass security software, Symantec experts claim.
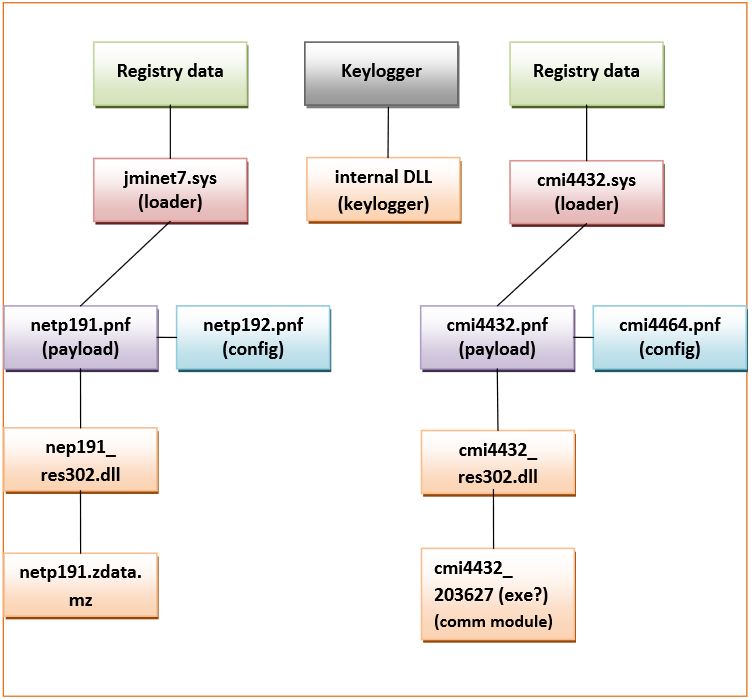
Below, we see a graph from the report, published along with the Symantec one from the experts who first discovered Duqu which outlines the files that were first found:
Figure 1: Components and modules discovered (http://www.crysys.hu/publications/files/bencsathPBF11duqu.pdf page 6)
In this situation experts noticed several different objects. The specifics about the keylogger in the software is that it is a standalone application that uses its internal DLL which collects date and is controlled by the .exe file.
The jminet7.sys and cmi4432.sys loaders are very similar to one another because they both load their versions of .sys drivers at the time when Windows boots. Other activities include the creation of the encrypted files netp192.pnf and cmi4464.pnf that store data. It is possible that they have some support role or scripts to install files such as a keylogger, etc.
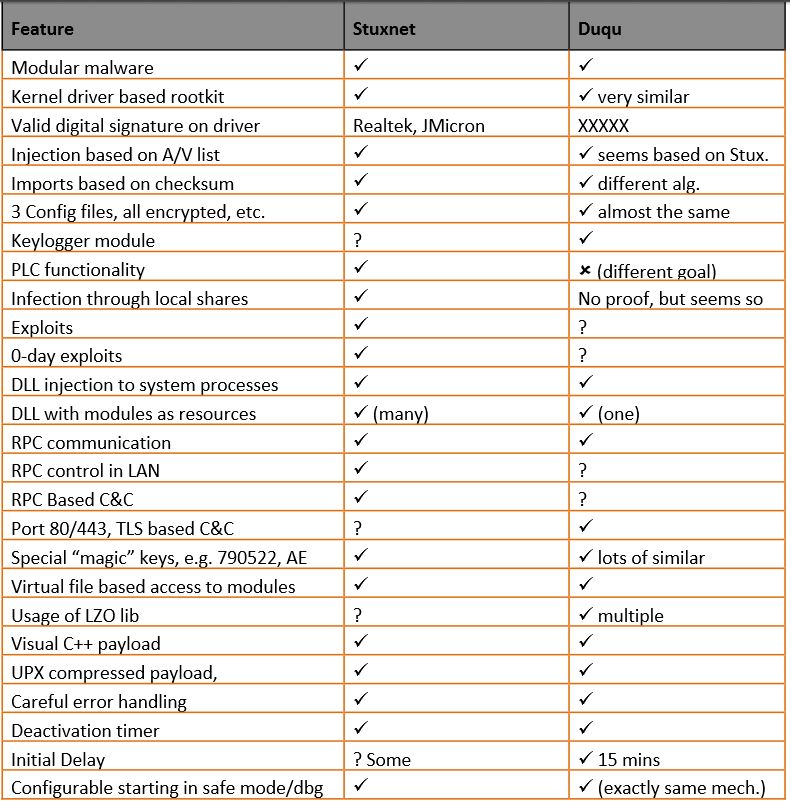
It was also interesting when Duqu was compared to its predecessor Stuxnet as shown below.
Figure 2:Comparison between Duqu and Stuxnet (http://www.crysys.hu/publications/files/bencsathPBF11duqu.pdf page 8)
As visible there have been many similarities uncovered, however with the 2.0 version, there are some changes in the code, compared to the 1.0.
Figure 3. Duqu vs Duqu 2.0 network code (http://www.symantec.com/connect/blogs/duqu-20-reemergence-aggressive-cyberespionage-threat)
Experts believe that Duqu has been evolved by most likely a group of people with the purpose of staying undetected for a longer lifespan. When a program such as Duqu 2 is designed to obtain data from a system, good ethics are to make the gotten information easily accessible. 1.0 and 2.0 share similar portions of that very information storage code.
Duqu 2.0 Impact
When it first discovered in 2011 in two variants, the malware infected six organizations in eight different countries, situated on 3 continents, and most attacks were located in Europe. It’s so called predecessor Stuxnet was analysed worldwide by security experts and commented widely over the media. Security researchers from Kaspersky claimed that they were not yet able to tell about the full scope of impact of the virus, since there aren`t any significant systems that were affected by it.