A ransomware virus, named .MOLE file virus has been reported to be deriving from the CryptoMix ransomware versions. The virus aims to perform different activities on compromised computers, the main of which is to encrypt the files on the ones infected by it. The virus then may drop a ransom note where demands are stated to pay a hefty ransom fee to restore files encrypted with the .MOLE file extension added to them.
.MOLE Virus File – What Does It Do
As soon as it has infected a given computer, the MOLE ransomware virus begins to display a fake Windows pop-up that states that the color management of Windows cannot control and calibrate the display. After the victim clicks “OK” on the spammed message, the virus will start the UAC service which asks the user to approve an administrative command to execute an executable file, named pluginoffice.exe:
”C:\Windows\SysWOW64\wbem\WMIC.exe” process call create “%UserProfile%\pluginoffice.exe”
As soon as this file is executed it obtains administrative rights over the infected computer. Then, the following Windows processes are stopped:
- Wscsvc
- WinDefend
- Wuauserv
- BITS
- ERSvc
- WerSvc
Then, .MOLE ransomware virus will begin the encryption process. For the encryption to work, the virus scans for multiple files of importance in order to encipher them. Malware researchers, report the files targeted by .MOLE virus to be the following:
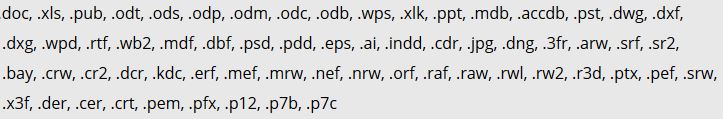
Source: Symantec Threat Response
After the encryption process has completed, .MOLE file virus leaves the encrypted files with the .MOLE file extension, for example.
- New Text Document.txt.MOLE
After this, the .MOLE ransomware deletes the volume shadow copies of the infected computer, by executing the VSSADMIN command as administrator in Windows command prompt. This makes the file recovery even less probable.
After the encryption process has completed, .MOLE Ransomware drops a ransom note, named INSTRUCTION_FOR_HELPING_FILE_RECOVERY.txt which has the following message:
.MOLE Ransomware – How Did I Get Infected
Your computer may have been compromised if you have received a suspicious e-mail sent by multiple different sources that pretend to be a legitimate services, like the reported USPS e-mails with the following message:
“Hello,
We can not deliver your parcel arrived at [DATE+TIME].You can find additional information by clicking on the following link.
[MALICIOUS URL]Best regards.
Maiqula Lohmiller – USPS Parcels Delivery Agent.”
These e-mails may point out to a fake web page, displaying a locked Microsoft office document and asking to download the file in order to read it’s content. The web page may really resemble a web page from the online service Office365.
Once the victim downloads and executes the files, the infection by .MOLE ransomware is inevitable.
Remove .MOLE Ransomware and Get The Data Back
For the removal of .MOLE virus files, we suggest you to follow the instructions below. In case you are experiencing difficulties in manually removing .MOLE ransomware, experts always advise to download anti-malware software. Such will not only automatically remove all files and registry objects associated with the .MOLE virus from your computer but will also make sure your system is protected actively. After removing mole, please see our suggestions on how to get your files back below.
Booting in Safe Mode
For Windows:
1) Hold Windows Key and R
2) A run Window will appear, in it type “msconfig” and hit Enter
3) After the Window appears go to the Boot tab and select Safe Boot
Cut out .MOLE File Virus in Task Manager
1) Press CTRL+ESC+SHIFT at the same time.
2) Locate the “Processes” tab.
3) Locate the malicious process of .MOLE File Virus, and end it’s task by right-clicking on it and clicking on “End Process”
Eliminate .MOLE File Virus‘s Malicious Registries
For most Windows variants:
1) Hold Windows Button and R.
2) In the “Run” box type “Regedit” and hit “Enter”.
3) Hold CTRL+F keys and type .MOLE File Virus or the file name of the malicious executable of the virus which is usually located in %AppData%, %Temp%, %Local%, %Roaming% or %SystemDrive%.
4) After having located malicious registry objects, some of which are usually in the Run and RunOnce subkeys delete them ermanently and restart your computer. Here is how to find and delete keys for different versions.
For Windows 7: Open the Start Menu and in the search type and type regedit –> Open it. –> Hold CTRL + F buttons –> Type .MOLE File Virus Virus in the search field.
Win 8/10 users: Start Button –> Choose Run –> type regedit –> Hit Enter -> Press CTRL + F buttons. Type .MOLE File Virus in the search field.
Automatic Removal of .MOLE File Virus
Recover files encrypted by the .MOLE File Virus Ransomware.
Method 1: Using Shadow Explorer. In case you have enabled File history on your Windows Machine one thing you can do is to use Shadow Explorer to get your files back. Unfortunately some ransomware viruses may delete those shadow volume copies with an administrative command to prevent you from doing just that.
Method 2: If you try to decrypt your files using third-party decryption tools. There are many antivirus providers who have decrypted multiple ransomware viruses the last couple of years and posted decryptors for them. Chances are if your ransomware virus uses the same encryption code used by a decryptable virus, you may get the files back. However, this is also not a guarantee, so you might want to try this method with copies of the original encrypted files, because if a third-party program tampers with their encrypted structure, they may be damaged permanently. Here are the vendors to look for:
- Kaspersky.
- Emsisoft.
- TrendMicro.
Method 3: Using Data Recovery tools. This method is suggested by multiple experts in the field. It can be used to scan your hard drive’s sectors and hence scramble the encrypted files anew as if they were deleted. Most ransomware viruses usually delete a file and create an encrypted copy to prevent such programs for restoring the files, but not all are this sophisticated. So you may have a chance of restoring some of your files with this method. Here are several data recovery programs which you can try and restore at least some of your files:

