A new variant of the infamous Locky ransomware has been recently unleashed worldwide – its name is Zepto and it uses the same ransom note as that of its predecessor. Moreover, it adds the .zepto extension to the encrypted files.
Zepto Ransomware – How Does It Enter Your PC?
Much like Locky, Zepto sneaks into users’ computers via spam emails containing a compromised JavaScript file. Upon opening, the virus downloads to the computer and the infection begins. Similarly to other ransomware infections, the process of encryption occurs quietly in the background so the victim has no way of detecting it until the process is complete and it’s too late to take precaution.
Zepto Ransomware – What Does It Do?
Once Zepto is inside the victim’s system, it will initiate a scanning process to detect files for encryption. Such files are:
123, .3dm, .3ds, .3g2, .3gp, .602, .aes, .arc, .asc, .asf, .asm, .asp, .avi, .bak, .bat, .bmp, .brd, .cgm, .cmd, .cpp, .crt, .csr, .csv, .dbf, .dch, .dif, .dip,
.djv, .djvu, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .fla, .flv, .frm, .gif, .gpg, .hwp, .ibd, .jar, .java, .jpeg, .jpg, .key, .lay, .lay6, .ldf, .m3u, .m4u, .max, .mdb, .mdf, .mid, .mkv, .mov, .mp3, .mp4, .mpeg, .mpg, .ms11, .myf, .myi, .nef, .odb, .odg, .odp, .ods, .odt, .otg, .otp, .ots, .ott, .p12, .paq, .pas, .pdf, .pem, .php, .png, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .psd, .rar, .raw, .rtf, .sch, .sldm, .sldx, .slk, .stc, .std, .sti, .stw, .svg, .swf, .sxc, .sxd, .sxi, .sxm, .sxw, .tar, .tbk, .tgz, .tif, .tiff, .txt, .uop, .uot, .vbs, .vdi, .vmdk, .vmx, .vob, .wav, .wb2, .wk1, .wks, .wma, .wmv, .xlc, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .zip
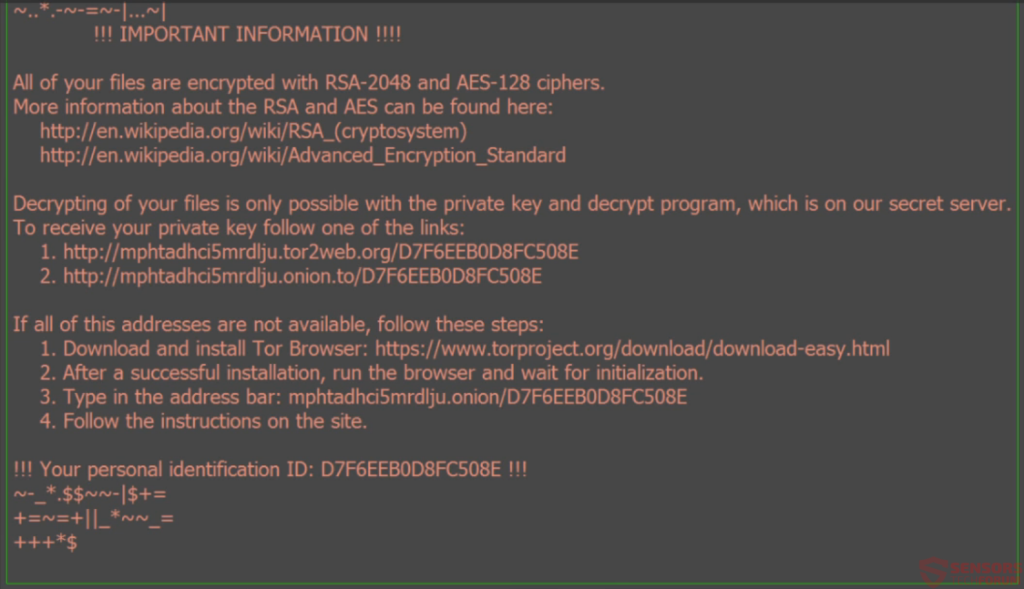
Once the encryption process is complete, Zepto will turn the desktop’s image into a ransom note that looks like that:
It says:
!!! IMPORTANT INFORMATION !!!
All of your files are encrypted with RSA-2048 and AES-128 ciphers.
More information about the RSA and AES can be found here:
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Decrypting of your files is only possible with the private key and decrypt program, All which is on our secret server.
To receive your private key follow one of the links:
1. http://mphtadhci5mrdlju.tor2web(.)org/D7F6EEB0D8FC508E
2. http://mphtadhci5mrdlju.onion(.)to/D7F6EEB0D8FC508E
If all of this addresses are not available, follow synthesis steps:
1. Download and install Tor Browser: https://www.torproject.org/download/download-easy(.)html
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar: mphtadhci5mrdlju(.)onion/D7F6EEB0D8FC508E
4. Follow the instructions on the site.
!!! Your personal identification ID: D7F6EEB0D8FC508E !!!
As the ransom message says, Zepto virus uses RSA-2048 and AES-128 ciphers for file encryption. The amount demanded from the victim is 0.5 bitcoins (or 315 US dollars)
Zepto Ransomware – How to Remove It
If you have been attacked by Zepto virus, you must first remove it from your system. To do that, make sure you use a powerful anti-malware tool that will scan your computer and clean the malicious components from it. Only then you can try to restore some of your files via file recovery tools. It’s no lie that once the files have been scrambled by a ransomware infection from the rank of Zepto, Locky, Cerber, etc., it’s almost impossible to restore any of them. Paying the cyber crooks in an exchange for a decryption key, however, is also not the solution since the virus remains in your system and could strike back any time.