 Other variant of the devastating Locky ransomware virus has been detected by malware researchers out in the open to demand the sum of 3 BTC as a ransom on infected computers. The virus is focused primarily on encrypting files of the victims’ computers after which leaving them with the .osiris file extension. This variant differs by most Locky ransomware variants mainly by some additions to the methods of distribution of the virus and the file extension, using an Egyptian god instead of the occasional Norse gods used in the previous versions of the malware.
Other variant of the devastating Locky ransomware virus has been detected by malware researchers out in the open to demand the sum of 3 BTC as a ransom on infected computers. The virus is focused primarily on encrypting files of the victims’ computers after which leaving them with the .osiris file extension. This variant differs by most Locky ransomware variants mainly by some additions to the methods of distribution of the virus and the file extension, using an Egyptian god instead of the occasional Norse gods used in the previous versions of the malware.
Locky .osiris File Virus – How Does It Infect
The creators of Locky ransomware have stuck to the well-known method of spreading the malware, using spam campaigns to replicate it via e-mail. E-mail messages used by the creators of Locky are considered to be the primary threat to users. The e-mails are reported to contain the following type of files that cause the infection:
- .xls file with a random name such as _2234_214252_
- .js and .wsf (JavaScript)
- .hta, .html, .htm (lead to malicious web hosts)
- .vbs (Visual Basic Script) that causes direct infection
These files are usually stored in archives such as .zip or .rar archives that have similar or the same names as the attachments to avoid detection by e-mail providers’ security. The latest Locky variant using the .osiris file extension has been reported to use a file, named as “Osiris.htm” or an “.xls” file with random numbers as a name.
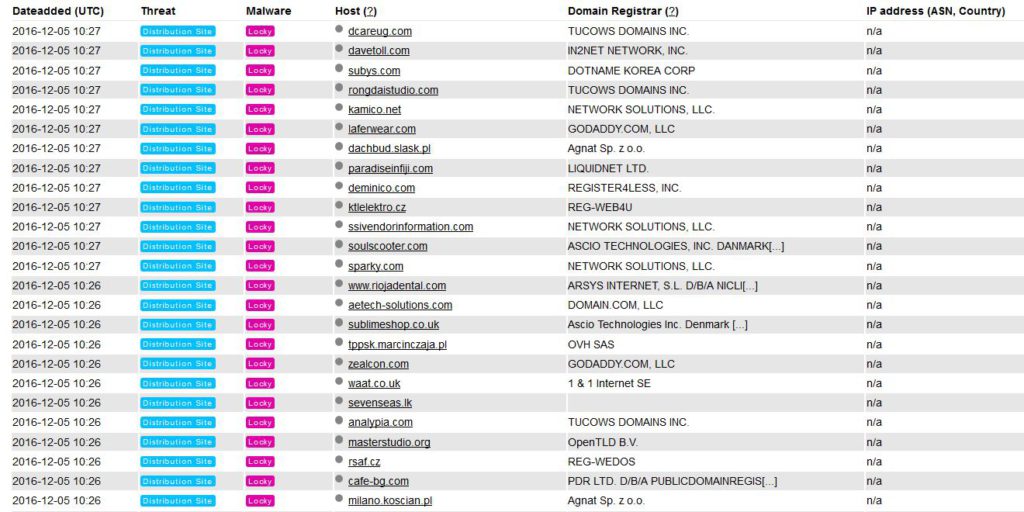
Once the user clicks on the file, obfuscated actions may immediately connect to one of the many Locky distribution websites:
After having connected to those webistes, the malware may download an obfuscated payload in crucial Windows folders, like the previously detected by Hybrid-Analysis a1.exe containing Locky, located in %Temp%.
So far it is reported to be pre-configured in order to encrypt file types that are the same as the previous versions, like the .aesir, .shit, .zzzzz Locky variants. This includes encrypting most often met file formats of:
- Images.
- Videos.
- Virtual drives.
- Database files.
- Files that are associated with Microsoft Word.
- Microsoft Excel files.
- Files associated with Adobe Reader.
- Files that have something In common with most virtual drive players.
Once Locky .osiris infects those files, the virus begins to replace the code of those files with custom symbols belonging to a very strong encryption algorithm, called AES-128. These files then generate unique decryption key. After this pass, the virus makes another pass using the also very advanced RSA-2048 encryption algorithm with the one and only purpose of generating unique RSA public and private keys. The virus then may either connect to the c2 servers and send the decryption keys on them or keep them on the infected computer for a specific Locky Decryptor which is sold for BTC. Encrypted files look like the below mentioned example:
After encryption by this Locky ransomware virus has completed, the virus begins to immediately display a “Read Me” .htm file that has the following instructions:
“All of your files are encrypted with RSA-2048 and AES-128 ciphers.
More information about the RSA and AES can be found here:
{links to Wikipedia}
Decrypting of your files is only possible with the private key and decrypt program, which is on our secret servers. To receive your private key follow one of the links:
If all of this addresses are not available, follow these steps:
1. Download and install tor Browser: https://www.torproject.org/download/download-easy.html
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar: {unique Locky URL}
4. Follow the instructions on the site.”
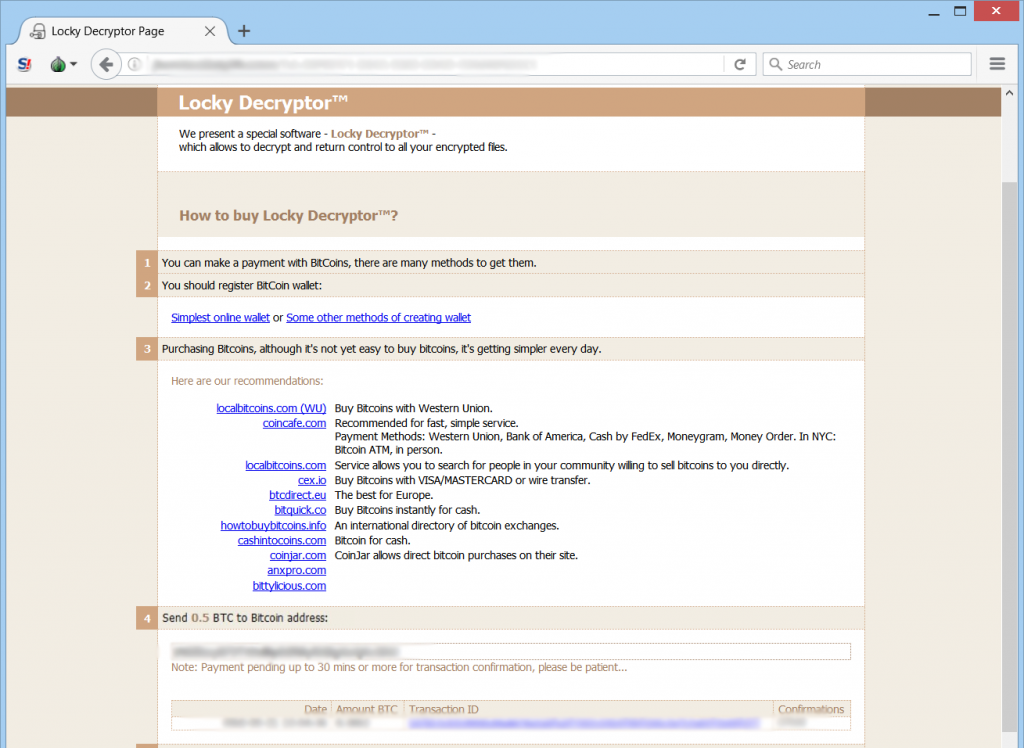
The instructions on the website are the standard Locky Decryptor instructions which are used in most of it’s variants – a web page with instructions on how to buy BitCoin and pay for a “Locky Decryptor”:
In addition to this the files OSIRIS-{RAND}.htm and shtefans1.spe are also added on the infected computer amongst other files.
How to Remove Locky .osiris Virus and Restore My Files
In case you feel like not paying any ransom to cyber-criminals that may or may not get your files back, we strongly advise you to firstly remove Locky from your computer after which focus on trying to restore your files using alternative methods. For the safest and best removal of Locky .osiris ransomware experts strongly advise using an advanced anti-malware tool that will automatically take care of all the objects Locky ransomware has interfered with.
We advise you to carefully follow the below mentioned steps in order to remove Locky .osiris properly:
Step 1: Download and install an advanced anti-malware program:
Step 2: Boot your computer in Safe-Mode and scan it with the program to remove Locky .osiris iteration.
Step 3: Using Data Recovery tools. This method is suggested by multiple experts in the field. It can be used to scan your hard drive’s sectors and hence scramble the encrypted files anew as if they were deleted. Most ransomware viruses usually delete a file and create an encrypted copy to prevent such programs for restoring the files, but not all are this sophisticated. So you may have a chance of restoring some of your files with this method. Here are several data recovery programs which you can try and restore at least some of your files: