Cerber Ransomware has been recently reborn. It’s now raging around under the name of Cerber2 – its new and improved version. The new name, however, is not the only difference between the old and the new variants. Read further to find out how Cerber2 acts now and how you can remove it and restore your files.
Cerber2 Ransomware – How Does It Enter Your Computer?
Cerber2’s delivery method is no different than most ransomware viruses, including its predecessor. It spreads mainly via spam emails which contain an executable with the icon of “Anka” (a video game character), and once you open the file, Cerber2 downloads to your system and the infection begins. Other means of delivery, however, are also possible, i.e. via social networks, file-sharing services, exploit kits, etc.
To trick users into opening a compromised email, cyber crooks usually use familiar for the user sender names such as invoices from banks, popular websites, etc. We advise all users to be extra alert when checking their inboxes and when receiving files from suspicious senders. If you have the slightest doubt about the email/file you are about to open, don’t do it, as the ransomware will enter your system with the blink of an eye and it will scramble your important files for good.
Cerber2 Ransomware – What Does It Do?
Once you have clicked a compromised file containing Cerber2, it enters your system and gets activated just like its predecessor. It will then scan your whole system to look for files with the following extensions to encrypt them:
1cd, .3dm, .3ds, .3fr, .3g2, .3gp, .3pr, .7z, .7zip, .aac, .ab4, .abd, .acc, .accdb, .accde, .accdr, .accdt, .ach, .acr, .act, .adb, .adp, .ads, .agdl, .ai, .aiff, .ait, .al, .aoi, .apj, .apk, .arw, .ascx, .asf, .asm, .asp, .aspx, .asset, .asx, .atb, .avi, .awg, .back, .backup, .backupdb, .bak, .bank, .bay, .bdb, .bgt, .bik, .bin, .bkp, .blend, .bmp, .bpw, .bsa, .c, .cash, .cdb, .cdf, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cer, .cfg, .cfn, .cgm, .cib, .class, .cls, .cmt, .config, .contact, .cpi, .cpp, .cr2, .craw, .crt, .crw, .cry, .cs, .csh, .csl, .css, .csv, .d3dbsp, .dac, .das, .dat, .db, .db_journal, .db3, .dbf, .dbx, .dc2, .dcr, .dcs, .ddd, .ddoc, .ddrw, .dds, .def, .der, .des, .design, .dgc, .dgn, .dit, .djvu, .dng, .doc, .docm, .docx, .dot, .dotm, .dotx, .drf, .drw, .dtd, .dwg, .dxb, .dxf, .dxg, .edb, .eml, .eps, .erbsql, .erf, .exf, .fdb, .ffd, .fff, .fh, .fhd, .fla, .flac, .flb, .flf, .flv, .flvv, .forge, .fpx, .fxg, .gbr, .gho, .gif, .gray, .grey, .groups, .gry, .h, .hbk, .hdd, .hpp, .html, .ibank, .ibd, .ibz, .idx, .iif, .iiq, .incpas, .indd, .info, .info_, .ini, .iwi, .jar, .java, .jnt, .jpe, .jpeg, .jpg, .js, .json, .k2p, .kc2, .kdbx, .kdc, .key, .kpdx, .kwm, .laccdb, .lbf, .lck, .ldf, .lit, .litemod, .litesql, .lock, .log, .ltx, .lua, .m, .m2ts, .m3u, .m4a, .m4p, .m4v, .ma, .mab, .mapimail, .max, .mbx, .md, .mdb, .mdc, .mdf, .mef, .mfw, .mid, .mkv, .mlb, .mmw, .mny, .money, .moneywell, .mos, .mov, .mp3, .mp4, .mpeg, .mpg, .mrw, .msf, .msg, .myd, .nd, .ndd, .ndf, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nvram, .nwb, .nx2, .nxl, .nyf, .oab, .obj, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .ogg, .oil, .omg, .one, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pab, .pages, .pas, .pat, .pbf, .pcd, .pct, .pdb, .pdd, .pdf, .pef, .pem, .pfx, .php, .pif, .pl, .plc, .plus_muhd, .pm!, .pm, .pmi, .pmj, .pml, .pmm, .pmo, .pmr, .pnc, .pnd, .png, .pnx, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx,.ppt, .pptm, .pptx, .prf, .private, .ps, .psafe3, .psd, .pspimage, .pst, .ptx, .pub, .pwm, .py, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .qcow, .qcow2, .qed, .qtb, .r3d, .raf, .rar, .rat, .raw, .rdb, .re4, .rm, .rtf, .rvt, .rw2, .rwl, .rwz, .s3db, .safe, .sas7bdat, .sav, .save, .say, .sd0, .sda, .sdb, .sdf, .sh, .sldm, .sldx, .slm, .sql, .sqlite, .sqlite3, .sqlitedb, .sqlite-shm, .sqlite-wal, .sr2, .srb, .srf, .srs, .srt, .srw, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stl, .stm, .stw, .stx, .svg, .swf, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .tax, .tbb, .tbk, .tbn, .tex, .tga, .thm, .tif, .tiff, .tlg, .tlx, .txt, .upk, .usr, .vbox, .vdi, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .vob, .vpd, .vsd, .wab, .wad, .wallet, .war, .wav, .wb2, .wma, .wmf, .wmv, .wpd, .wps, .x11, .x3f, .xis, .xla, .xlam, .xlk, .xlm, .xlr, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xps, .xxx, .ycbcra, .yuv, .zip
Cerber2 is capable of encrypting over 450 file types. You know your files have been locked by Cerbe2 when they receive a .cerber2 extension at the end and the file names are replaced by such that contain ten random characters.
After the file encryption, Cerber2 will scan for certain processes, and if they are active, it shuts them down:
- excel.exe
- infopath.exe
- msaccess.exe
- mspub.exe
- onenote.exe
- outlook.exe
- powerpnt.exe
- steam.exe
- sqlservr.exe
- thebat.exe
- thebat64.exe
- thunderbird.exe
- visio.exe
- winword.exe
- wordpad.exe
As mentioned earlier, the name of this ransomware variant and the extensions its encrypted files receive, are not the only difference between Cerber and Cerber2 ransomware viruses. The most important improvement of the new one is that it no longer uses the AES-256 cypher as its main encryption technique. Rather, it uses the Microsoft’s CryptGenRansom.
Cerber2 also has a list of anti-malware programs that it’s immune to. These programs are:
- Arcabit
- Arcavir
- Avast
- BitDefender
- Bullguard
- EmsiSoft
- ESET
- eTrust
- F-Secure
- G Data
- Kaspersky Lab
- LavaSoft
- TrustPort
A countdown counter of a five-day “promotion” will then begin. The counter displays the deadline the victim has to pay the amount of 0.3 bitcoins (or 175 US dollars). If the victim does not make the transaction within 5 days, the amount doubles.
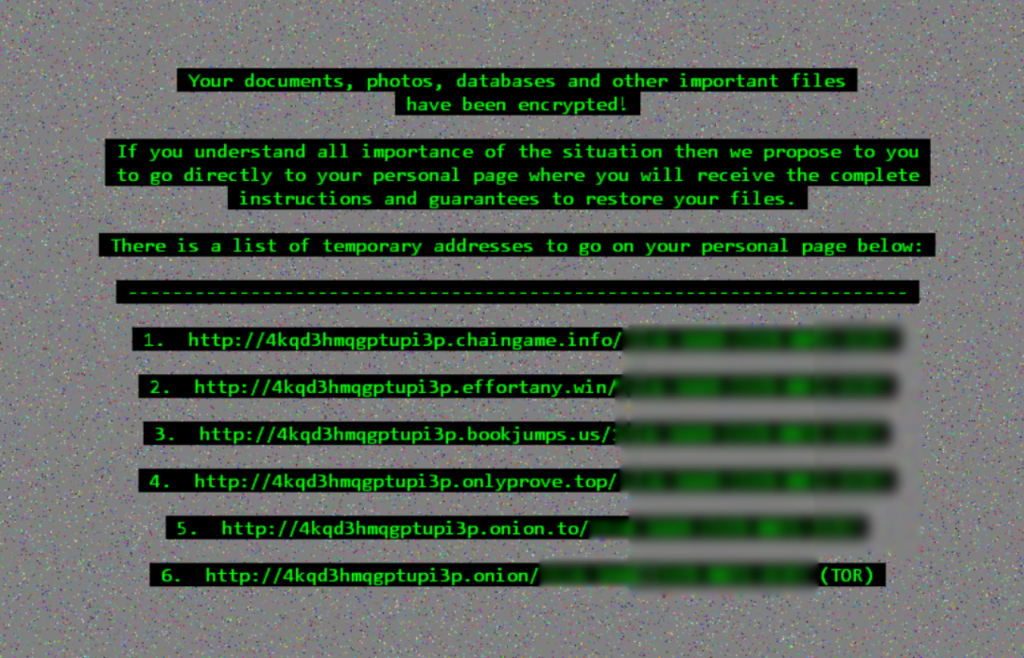
The ransom message looks like this:
…and it reads like this:
Your documents, photos, databases, and other important files have been encrypted!
If you understand all importance of the situation then we propose to you to go directly to your personal page where you will receive the complete instructions and guarantees to restore your files.
Cerber2 Ransomware – Manual Removal
Although it may sound tempting to just pay the ransom and get a decryption key for your files, we strongly urge you to not do it. Paying the cyber criminals does not guarantee you a decryption key, nor it ensures Cerber2’s removal. The virus will simply remain in your system and regardless of whether you have your files back, it may strike again.
Paying the cyber crooks only encourages them to spread the infection. Instead, we suggest that you use a powerful anti-malware tool that will scan your system, detect the virus and remove it permanently from your system. Once Cerber2 ransomware is fully removed from your PC, you can try to recover some of you files via file recovery tools.