Chtonic is using ZeusS code structure as a base, developing further features
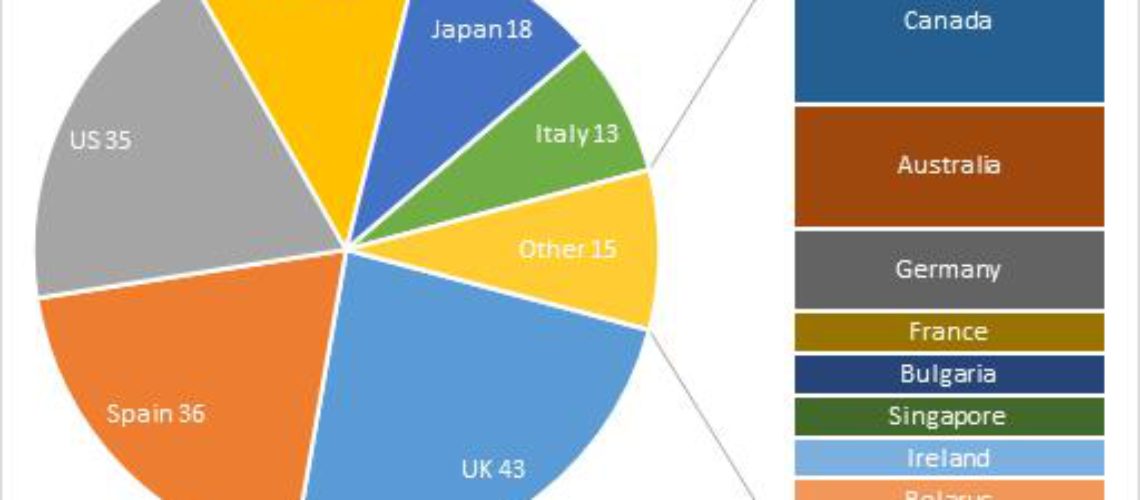
New Zeus Trojan banking software is spreading in the wild recently. Its configuration file seems to be targeting many European countries, thus pointing potentially at 150 banks and 20 payment systems. The malware has been spotted mostly in United Kingdom and Spain, but infections have been reported in other courtiers like Germany, France, Italy, Bulgaria and Ireland as well. According to researchers from Kaspersky Lab though, among the most affected countries are the United States, Russia and Japan.
The most spread out methods to be infected with Chthonic is through the infamous Andromeda botnet as well as through Microsoft Office vulnerability (CVE-2014-1761) which canec be received by mail as a specially designed RTF file. The file extension is changed to “.doc” to look less suspicious though.
Encryption
The Trojan activity has been spotted and described by Kaspersky Lab researchers in a blog post from last week. They state that the new Trojan uses encryption methods from other Zeus malware versions as well as from ZeusVM and KINS virtual machines. Another encryption method it uses is the same as the Andromeda botnet’s one, creating a botnet with the same name as well.
The malware has been called Chthonic and is based on a new module loading method. Chthonic seems to infiltrate a main module into the computer that continues downloading secondary ones after activation. All the modules are encrypted with AES specification, and most of the modules are compatible with both 32 and 64-bit systems.
The Trojan steals passwords through a Pony malware, records key computer activities (Keylogger) and injects machines through malicious websites and VNC remote desktop software.
Breach
Using a man-in-the-middle technique Chthonic violates the system by changing the targeted database. Users are being redirected to an infected web page. The malware continues then by stealing user sensitive data like username, password, PIN number, one-time password, etc. Fraud messages coming from the real webpage are being automatically hidden.
In some attacks in Russia, Kaspersky researchers said that it has been spotted the malware to spoof the entire content of the web page of the bank targeted and not just parts of it. This is not something typical for these types of attacks.
Although the many countries and banks targeted it seems that the Trojan cannot do much harm. As Zeus malwares are functioning for several years back many banks have changed the structure of their pages or their entire domains already. Many of the code fragments this Trojan is using seem to be pretty old.
Although it cannot do much harm at the moment, Zeus Trojan appears to be still evolving. Many of the malware developers are taking advantage of the fact that the ZeusS code source has been leaked and are using it as a base to develop their own Trojans for attacks. The new one – Chthonic – is using exactly this as a base to further evolve.