The malware researchers have registered a new cybercriminal campaign that is targeting the PC users, attacking them with Vawtrak baking Trojan. According to the security experts, the attackers use VBS file with execution policy bypass flag and rely on a compromise routine which includes usage of Microsoft Word documents that are connected with malicious macros. The banks that are targeted by the cyber criminals include Barclays and Bank of America, HSBC and Citibank, J.P. Morgan and Lloyd’s Bank.
Imperceptible tactics
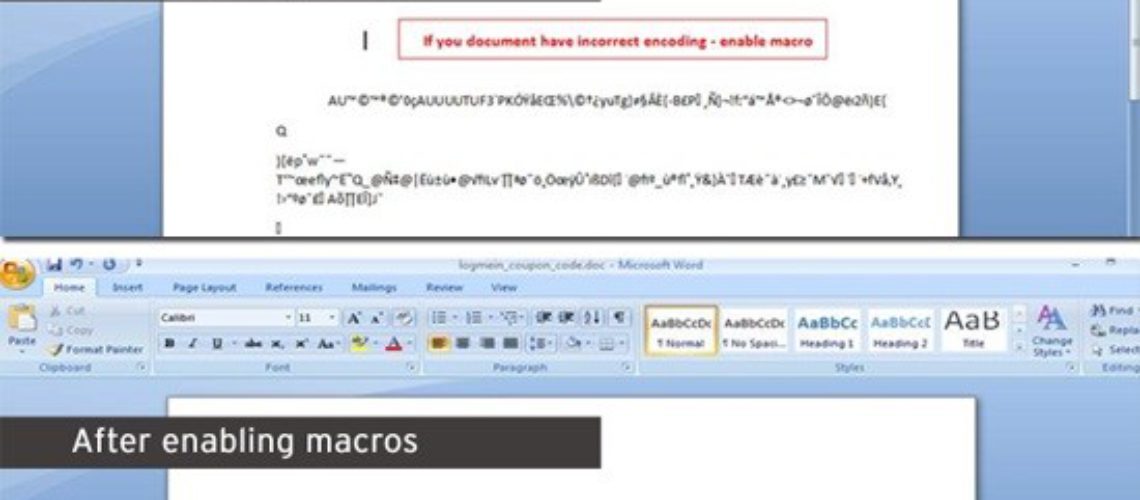
The cybercriminals are applying evasive and multiple tactics in order to hide the attack. One of the schemes they apply is to provide document content that looks scrambled and becomes clear only after a macro feature is used, found in the software component of Word. Another tactic is the delivery of VBS file which comes with an enabled flag for Execution Policy bypass. That flag is usually used by the system administrators in the form of a security mechanism in order to prevent users from launching scripts that do not comply with the policy requirements.
The bypass command scripts are allowed to execute files without issuing warnings and with no restrictions. The malicious emails that the users receive pretend to be coming from reputed services as FedEx or American Airlines, notifying the recipients about an arrival of a package or a transaction with their card. These messages come with an attachment – a document in Word that provides more details about the matter that is presented in the message.
As the victims open the text file, they are prompted to enable the macros – a collection of commands with legitimate purpose to run automated routines in an Office document. That feature is enabled by default by Microsoft in all Office components, as it started being abused by malicious actors. The users that need macros for automated tasks can enable these macros manually from the product.
With the current Vawtrak campaign the macro contains commands for downloading a VBS script, a batch file and a PowerShell file. The process goes like that – the batch file runs the VBS, and it turns it executes the PowerShell file which funnels the malware into the PC system. The cyber criminals use this three-step infection chain as an evasion tactic. This theory is further supported by the bypass execution flag that is set for the VBS script.
US users – most affected
According to the research of the malware experts, the Vawtrak pilfers log-in data is applied in Microsoft Outlook and the credentials stored in Google Chrome and Mozilla Firefox, and FTP clients. The Vawtrak Trojan was analyzed to hook into the web browser and bypass the SSL mechanism.
The cybercriminals run the connection to the bank through their infrastructure and serve the client with modified pages. In this way the victim is tricked into providing one’s two-step authentication code. Then it looks like as if the fraudulent transactions are carried out from the system of the victim.
This version of Vawtrak has infected mainly the users in the US (60 %), followed by the users in Japan (10 %), Germany (7 %), followed by United Kingdom (4.5 %) そして Australia (3.5 %).