Malware researchers have reported yet another version of the tireless CryptoLocker ransomware. The CryptoLocker-v3 ransomware has been detected in both Europe and USA. The malicious threat encrypts the files of the victim and generates a message demanding a ransom to be paid in order for the files to be decrypted.
CryptoLocker-V3 Ransomware Description
The CryptoLocker-v3 threat encrypts files with the following extensions:
.xls, .doc, .pdf, .rtf, .psd, .dwg, .cdr, .cd, .mdb, .1cd, .dbf, .sqlite, .jpg, .zip.
Once it is activated on the victim’s computer, it will start encrypting files matching the extensions mentioned above. Like most ransomware attacks, the CryptoLocker-v3 generates a unique public RSA-2048 key and a private RSA key, presumably used for file decryption after the demanded sum is paid.
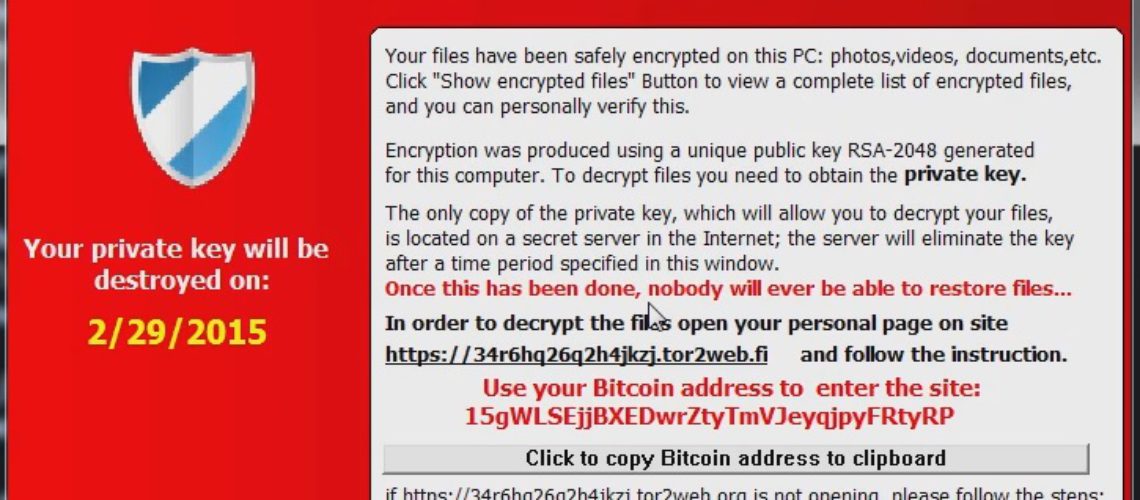
When the CryptoLocker-v3 parasite is running, it takes control of the attacked PC, thus the access to it is restricted. The ransomware then generates a desktop message stating that the victim’s personal files are ‘safely encrypted’. The creators of CryptoLocker-v3 have also provided a button that shows the encrypted files. As far as the payment, in the case of CryptoLocker-v3 BitCoin is used.
In the message displayed on the victim’s screen, the attackers warn that the private key will be eliminated after a certain period unless the ransom is paid. If the private key elimination occurs, no one will ever be able to restore the lost files.
In that relation, experts always recommend having your files stored on a separate device or in a cloud. That advice is especially useful for businesses since ransomware attackers mostly aim at companies. 幸運なことに, more and more businesses are concerned with privacy issues, as a security report on the matter recently revealed. More good news is on the way. Various tools for cyber crime prevention are also being developed. For instance, DeepCode is currently being designed by Cambridge University and Draper Laboratory.
CryptoLocker-v3 Ransomware Distribution
Security researchers have already discovered that CryptoLocker-v3 entirely copies the CryptoLocker. 実際には, the ransomware threat in question is also known as the TeslaCrypt. All versions of the CryptoLocker rely on Trojan tactics as distribution methods. That is why visiting any suspicious websites that may hide potential malware is not advisory.
Another way to prevent a ransomware attack from having a critical impact on your PC is safely storing your files elsewhere.