TorLocker, also known as Trojan-Ransom.Win32.Scraper, encrypts your files and offers a decryption key in an exchange for a ransom payment. Victims, however, can still gain access to their files without having to pay the ransom.
What Does Trojan-Ransom.Win32.Scraper Do?
As with any ransomware, Trojan-Ransom.Win32.Scraper enters your system solely because it wants your money. It locks your files, and it tells you can get them back only if you pay the demanded $300 or more.
The Trojan used to target Japanese users, but it is now aimed at English speaking users too. Kasperski have reported that it enters the victim’s computer via the Andromeda botnet.
According to Kasperski, “Our analysis has shown that Trojan-Ransom.Win32.Scraper was presumably written in assembler, which is unusual for this type of malware. The Trojan uses the Tor network to contact its “owners” – something that is apparently becoming a norm for the new generation of ransomware – and the proxy server polipo.”
The Flows in Trojan-Ransom.Win32.Scraper
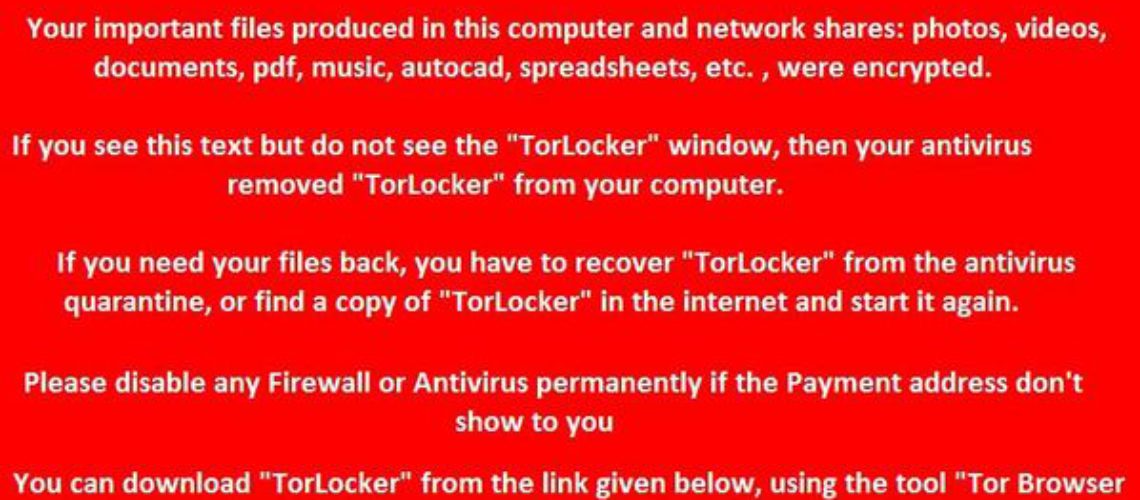
Kasperski researchers continued, “Trojan-Ransom.Win32.Scraper encrypts the victim’s documents and demands a ransom ($300 or greater) to decrypt them. If the malware gets deleted by a security product after the files are encrypted, the Trojan installs bright red wallpaper on the Desktop, containing a link to its executable file. Thus, users have a chance to re-install the Trojan and report to its owners that they have paid the ransom: to do so, users need to enter payment details in a dedicated TorLocker window.”
They did not specify the exact flows the malware developers had made but revealed that victims can decrypt over 70% of their locked files themselves.