Yet another version of the notorious Locky has been released. It is most likely an updated variant of the .aesir file extension Locky, similar to what Cerber ransomware, the other big player in this segment does, coming up with multiple variants in short timeframes. This variant of locky uses a .js file for the infection, but it does not have it’s own command servers and is instead automated, researchers believe. In order to understand how to remove this virus and learn alternative methods to try and restore your files without having to pay the ransom, we advise you to read this article thoroughly.
What Does Locky Ransomware Do?
When it infects, the Locky virus uses a different file extension to encrypt files, than it’s previous variants – .zzzzz. Unlike those variants which use the name of Norse gods, this Locky uses 1 letter repeated five times for an extension, which is untypical. Not only this, but e-mails that have archives, named order _{name of victim}.zip are utilized to infect users with malicious .js (JavaScript) files in them. The download locations of those files are one of the many distribution sites used by Locky.
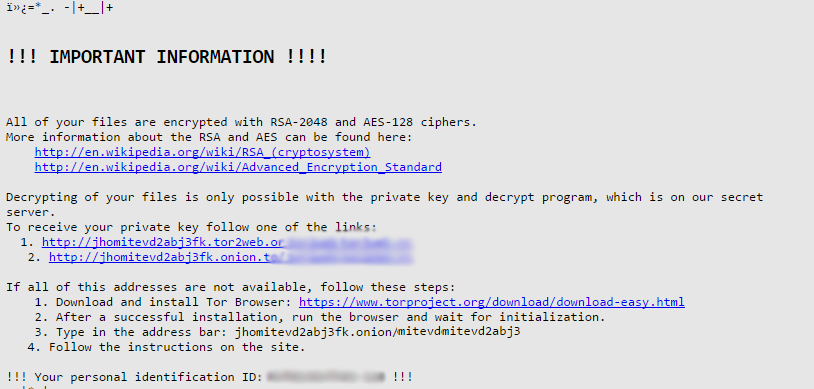
After this malicious file is opened by the user, the ransomware gets right down to business. It creates a copy of the ransom note use with the name _1-INSTRUCTION.html. The ransom note file is also changed as a background on the victim computer, looking like the following:
“!!! IMPORTANT INFORMATION !!!
All of your files are encrypted with RSA-2048 and AES-128 ciphers.
More information about the RSA and AES can be found here:
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Decrypting of your files is only possible with the private key and decrypt program, All which is on our secret server.
To receive your private key follow one of the links:
1. [Redacted] 2. [Redacted] If all of this addresses are not available, follow these steps:
1. Download and install Tor Browser: https://www.torproject.org/download/download-easy.html
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar: [Redacted] 4. Follow the instructions on the site.
!!! Your personal identification ID: [Redacted] !!!”
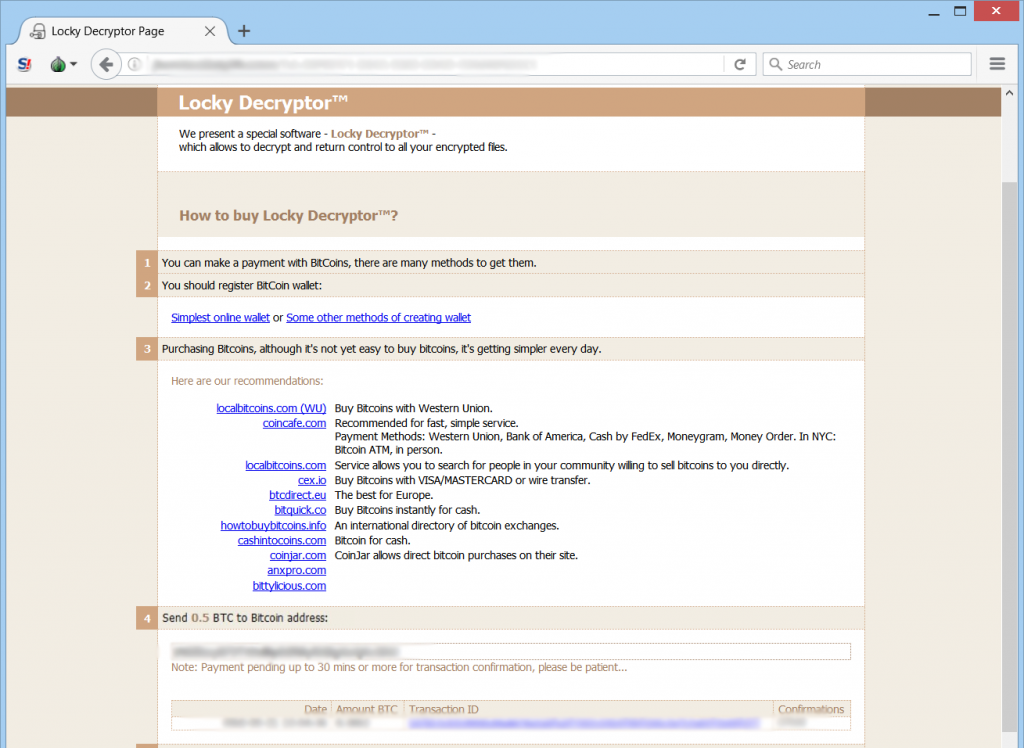
The INSTRUCTION.html file also has a similar ransom message:
Both sites aim to lead the victim whose files are encrypted by Locky’s .zzzzz variant to the traditional for this family of malware Locky Decryptor web page.
What Is Locky’s Encryption and Why I Cannot Open My Files?
The virus is one of the strongest when it comes to the encryption of the user files. In fact, it is pre-programmed to encrypt a wide variety of file extensions, more than 400:
→ .001, .002, .003, .004, .005, .006, .007, .008, .009, .010, .011, .123, .1cd, .3dm, .3ds, .3fr, .3g2, .3gp, .3pr, .602, .7z, .7zip, .ARC, .CSV, .DOC, .DOT, .MYD, .MYI, .NEF, .PAQ, .PPT, .RTF, .SQLITE3, .SQLITEDB, .XLS, .aac, .ab4, .accdb, .accde, .accdr, .accdt, .ach, .acr, .act, .adb, .adp, .ads, .aes, .agdl, .ai, .aiff, .ait, .al, .aoi, .apj, .apk, .arw, .asc, .asf, .asm, .asp, .aspx, .asset, .asx, .avi, .awg, .back, .backup, .backupdb, .bak, .bank, .bat, .bay, .bdb, .bgt, .bik, .bin, .bkp, .blend, .bmp, .bpw, .brd, .bsa, .cdf, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cer, .cfg, .cgm, .cib, .class, .cls, .cmd, .cmt, .config, .contact, .cpi, .cpp, .cr2, .craw, .crt, .crw, .cs, .csh, .csl, .csr, .css, .csv, .d3dbsp, .dac, .das, .dat, .db, .db3, .db_journal, .dbf, .dbx, .dc2, .dch, .dcr, .dcs, .ddd, .ddoc, .ddrw, .dds, .der, .des, .design, .dgc, .dif, .dip, .dit, .djv, .djvu, .dng, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .drf, .drw, .dtd, .dwg, .dxb, .dxf, .dxg, .edb, .eml, .eps, .erbsql, .erf, .exf, .fdb, .ffd, .fff, .fh, .fhd, .fla, .flac, .flf, .flv, .flvv, .forge, .fpx, .frm, .fxg, .gif, .gpg, .gray, .grey, .groups, .gry, .gz, .hbk, .hdd, .hpp, .html, .hwp, .ibank, .ibd, .ibz, .idx, .iif, .iiq, .incpas, .indd, .iwi, .jar, .java, .jnt, .jpe, .jpeg, .jpg, .js, .kc2, .kdbx, .kdc, .key, .kpdx, .kwm, .laccdb, .lay, .lay6, .lbf, .ldf, .lit, .litemod, .litesql, .log, .ltx, .lua, .m2ts, .m3u, .m4a, .m4p, .m4u, .m4v, .mapimail, .max, .mbx, .md, .mdb, .mdc, .mdf, .mef, .mfw, .mid, .mkv, .mlb, .mml, .mmw, .mny, .moneywell, .mos, .mov, .mp3, .mp4, .mpeg, .mpg, .mrw, .ms11, .msg, .myd, .n64, .nd, .ndd, .ndf, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nvram, .nwb, .nx2, .nxl, .nyf, .oab, .obj, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .ogg, .oil, .onetoc2, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pab, .pages, .pas, .pat, .pcd, .pct, .pdb, .pdd, .pdf, .pef, .pem, .pfx, .php, .pif, .pl, .plc, .plus_muhd, .png, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prf, .ps, .psafe3, .psd, .pspimage, .pst, .ptx, .pwm, .py, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .qcow, .qcow2, .qed, .r3d, .raf, .rar, .rat, .raw, .rb, .rdb, .re4, .rm, .rtf, .rvt, .rw2, .rwl, .rwz, .s3db, .safe, .sas7bdat, .sav, .save, .say, .sch, .sd0, .sda, .sdf, .sh, .sldm, .sldx, .slk, .sql, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srt, .srw, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stm, .stw, .stx, .svg, .swf, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .tar, .tar.bz2, .tbk, .tex, .tga, .tgz, .thm, .tif, .tiff, .tlg, .txt, .uop, .uot, .upk, .vb, .vbox, .vbs, .vdi, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .vob, .wab, .wad, .wallet, .wav, .wb2, .wk1, .wks, .wma, .wmv, .wpd, .wps, .x11, .x3f, .xis, .xla, .xlam, .xlc, .xlk, .xlm, .xlr, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .ycbcra, .yuv, .zip
Files that have been encrypted will have the file extension with the repeaded “z” letter and become no longer openable. The encryption believed to be used for those files is AES-128 in combination with a cipher that is RSA-2048 and produces a unique decryption key for each infection.
After this is done, Locky ransomware may delete backups and other file history using the vssadmin command.
How Did I Get Infected With Locky .zzzzz?
All that it takes to become infected with Locky ransomware’s .zzzzz variant is to open a phishing e-mail that pretends to be a legitimate one. Here is an example of an infection, discovered earlier:
→ “Dear Customer,
Greetings from Amazon.com
We are writing to let you know that the following item has been sent using Royal Mail.
For more information about delivery estimates and any open orders, please visit: {web link}
Your Order {order number}”
The e-mails have a malicious archive (.zip file) which is named “ORDER-{Number}.zip}”. If the user is inexperienced enough to download and open the malicious .js file in the archive which may pretend to be either a Microsoft Office or an Adobe document, they immediately become injected with a JavaScript protocol that causes the infection with Locky.
How To Remove Locky Ransomware and Restore Encrypted Files
In order to fully erase the virus we advise you to use an advanced anti-malware program in case you lack experience in malware removal. It will professionally delete all objects associated with Locky on your computer in a swift manner.
To try and restore your files you have several alternative methods lying before you:
- Data Recovery Software.
- Shadow Backups Restore (if intact)
- Network Sniffer.
- Try third party decryptors after backing up the encrypted files. (do not try them on the original copies of the encrypted files, only on other copies)
Those methods may not be 100% effective but they may be effective enough to restore at least some of your files.