 News broke out, that the latest 2016 version of Locky ransomware using the .zzzzz file extension has been spotter to spread in multiple new methods which has resulted in a recent increase of infections by this ransomware virus. For those uninformed, Locky is a ransomware virus which has cause a massive impact on computers worldwide, encrypting their important files and displaying a ransom note asking victims to pay money to restore the files. In case you have become a victim of this cyber-extortion we advise you to read this article and get familiar with how Locky infects to protect yourself in the future, preserve your files and also learn how to get rid of this nasty malware and alternative methods to restore your files.
News broke out, that the latest 2016 version of Locky ransomware using the .zzzzz file extension has been spotter to spread in multiple new methods which has resulted in a recent increase of infections by this ransomware virus. For those uninformed, Locky is a ransomware virus which has cause a massive impact on computers worldwide, encrypting their important files and displaying a ransom note asking victims to pay money to restore the files. In case you have become a victim of this cyber-extortion we advise you to read this article and get familiar with how Locky infects to protect yourself in the future, preserve your files and also learn how to get rid of this nasty malware and alternative methods to restore your files.
What Methods Does Locky Use to Infect
Method #1: Facebook SVG Images Spam
Several methods have been identified by malware researchers, and even a method of spreading this particular malware via Facebook as well. Despite Facebook denying the claims malware researchers feel convinced that .SVG images which were joined with the exploit kit dropping Locky ransomware via Nemucod malware.
This method is actually very smart and unique, because not only do files which are actual images and seem safe to be opened increase the infection possibility, but also fake Facebook profiles of friends and other users which may be in your circle may be used to send you message, further increasing trust.
Method #2: Via Fake Microsoft XLS Documents
Malware-Traffic-Analysis has recently discovered the new form of spamming e-mail attachments – Microsoft Excel files in a .xls file format. These files are often attached in massive spam e-mails which are regarded as INVOICES and copies of such. The researchers have discovered the following Invoice names related to the malware:
- COPY.{unique ID}.XLS
- INVOICE.TAM_{unique ID}.xls
The files were reported to be approximately 20 to 50 kilobytes in size and to be accompanied by spammed e-mails such as the following:
“Please find attached your Invoice for Goods/Services recently delivered. If you have any questions then pleasedo not hesitate in contacting us. Karen Lightfoot – CreditController, Ansell Lighting, Unit 6B, Stonecross Industrial Park, Yew Tree Way, WA3 3JD. Tel: +44 (0) 6477 609 803 Fax: +44 (0)6477 609 803”
Method #2: The Usage of Hidden Files
Locky has recently been reported to use file extensions that are connected with .JS or .EXE or .COM or .PIF or .SCR or .HTA .vbs, .wsf , .jse .jar types of files. Not only this, but the ransomware has also been reported to use several different types of obfuscators to hide those files and resemble them as invoices and other types of data. The spammers of the large network supporting the ransomware go as far as leaving fake phone numbers and names just to get users to click on the malicious files. This is mostly what other ransomware viruses do and it still remains to be very effective, even though now being classified as a well-known and mainstream infection tactic. Related to the latest malspam from .vbs detections are the following download hosts:
- sarawakcars.com/987t67g
- spunbaku.com/987t67g
- ryrszs.com/987t67g
- betagmino.net/987t67g
- renklerle.com/987t67g
- rotakin.org/987t67g
And not only this but Locky also changes the extensions of the file types, such as renaming a malicious .dll file to .tdb, .342 or other random 3 digit number of similarity.
Using .ZIP Archives To Infect with JavaScript
Locky is continuing to infect users is via using a malicious JavaScript files. Detections from the 29th of November 2016 show the following phishing message to spread a .Zip file, named “unpaid_{UniqueID or victim name}.zip”. The phishing e-mails have the following content:
“Greetings! You paid for yesterday’s invoice – the total sum was $3190.
Unfortunately, you hadn’t included the item #48047-61258 of $658.
Please transfer the remainder as soon as possible.”
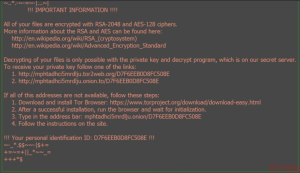
Locky .zzzzz Ransowmare – Removal, Protection and File Restoration
It is obvious that once Locky attacks your computer, the files become encrypted and have the added .zzzzz file extensions. Since the ransomware changes the wallpaper with instructions on a Tor-based web page, researchers advise avoiding those instructions and focusing on proactive actions against this malware.
First, it is important to remove Locky ransomware from your computer. You can interfere with the registry entries and other data manually, but you also have the option to take an automatic approach which is what experts recommend. This approach involves the simple download and scan of your computer using an advanced anti-malware software which will further protect your computer from future threats as well.
In addition to this, Locky ransomware also encrypts the files, rendering them no longer openable. The most appropriate way to address this issue without having to pay any ransom is to focus on following the below- mentioned alternative methods for file restoration.
