 New version of the notorious Locky ransomware has appeared, appending the .thor file extension. The variant immediately popped out after another variant that uses the .shit file extension exploded with infections in different countries all over the world. The .thor version of Locky is very dangerous and if detected, advice is to remove it on sight with an anti-malware program and not pay the ransom requested of 0.5 BTC.
New version of the notorious Locky ransomware has appeared, appending the .thor file extension. The variant immediately popped out after another variant that uses the .shit file extension exploded with infections in different countries all over the world. The .thor version of Locky is very dangerous and if detected, advice is to remove it on sight with an anti-malware program and not pay the ransom requested of 0.5 BTC.
Download Malware Removal Tool, to See If Your System Has Been Affected By Locky Ransomware Virus and scan your system for .SHIT virus files
Locky .thor Variant – What Does It Do (Methodological Description)
The first stage of the ransomware virus is for it to be widespread. For this to be achieved, the creators of the virus have used a rather cunning but expected delivery method. They use spam e-mail messages with different contant that aim to trick unexperienced users into opening an archived file with name, similar to the following:
After the archived file has been opened, it may contain a file that is one of the following file types
Once the user opens this file, the infection process has started. The infection file connects remotely to a one of hundreds of hosts to download the payload of the .thor Variant of Locky ransomware.
Once the payload file has been downloaded, the ransomware virus immediately becomes active by beginning to modify Windows settings.
Initially it connects to the command and control servers to begin relying information live as to whether or not the infection is successful and what the malicious user wants to be done with the infected computer. The command centers of Locky have so far been reported to hide behind the following domains:
fvhnnhggmck.ru/linuxsucks.php
krtwpukq.su/linuxsucks.php
tdlqkewyjwakpru.ru/linuxsucks.php
185.102.136.77:80/linuxsucks.php
91.200.14.124:80/linuxsucks.php
91.226.92.225:80/linuxsucks.php
77.123.14.137:221/linuxsucks.php
Amongst the dropped files of Locky Ransowmare is the .dll file that is responsible for the file encryption. The virus may immediately execute the file, something that may also be known as a drive-by-download. However, the .thor variant of Locky can also drop the file in %Startup% directory or modify the Run and RunOnce registry keys so that the encryptor runs on Windows startup.
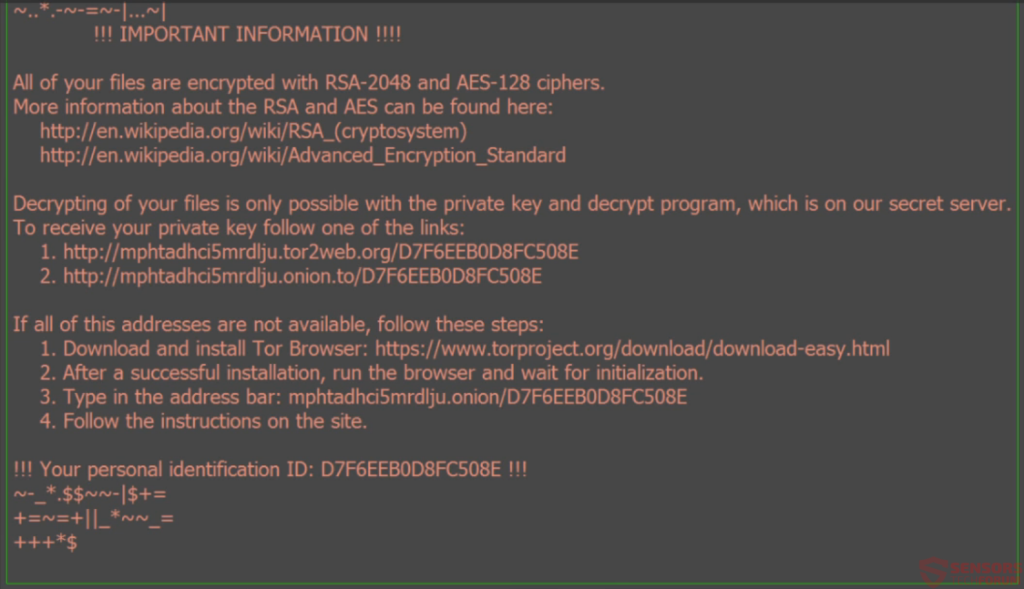
After encryption has been ran, just like the .shit file extension variant of Locky, this variant may also wreak havoc on your computer. It immediately drops it’s unique ransom notes, which are a wallpaper and a _WHAT_is.html file.
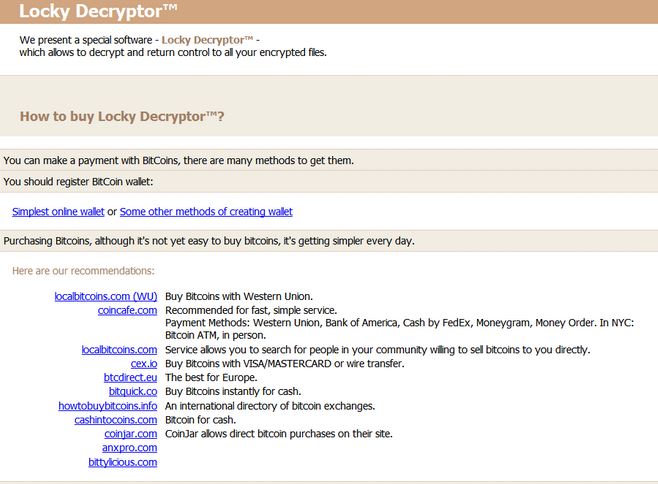
The note on both leads to a unique URL belonging to Locky ransomware which has more instructions on how to create a BitCoin wallet and pay the ransom this way.
After the encryption has been done, the .thor Variant of Locky makes sure the original versions of the files are gone for good, by creating copies of the encrypted files and “running over” the original files via several passes for deletion. It also erases Shadow Volume copies, just in case there are some with the following command injected via Windows Command Prompt.
How Do I Remove Locky Ransomware and Decrypt .thor Files?
Unfortunately for all of the Locky variants, there has not been discovered a single file decryption. You can, however perform several other tasks, such as attempt to find the decryption key corresponding to the encryptor of Locky that has encrypted your files and made them look like the following:
One method to do this is via a network sniffing software, however you have to catch the moment when the malware sends information via HTTP, UDP or TCP to the malicious C2 server.
Another way of getting the key is by paying the ransom which is not recommended. Instead you can try to use data recovery software and attempt to restore some of your files by scanning the sectors of your hard drive.
Download Malware Removal Tool, to See If Your System Has Been Affected By Locky Ransomware Virus and scan your system for .SHIT virus files