A virus, dubbed as KillerLocker by malware researchers was detected in malicious executables. The virus displays a ransom note with a clown in Portuguese and gives 48 hours to the victims to get into contact to cyber-crooks and pay a hefty ransom fee. To lock the files of infected computers, KillerLocker uses an AES cipher with 256 bit strength. It also adds the .rip file extension after it encrypts user files.
KillerLocker Ransowmare – Further Information
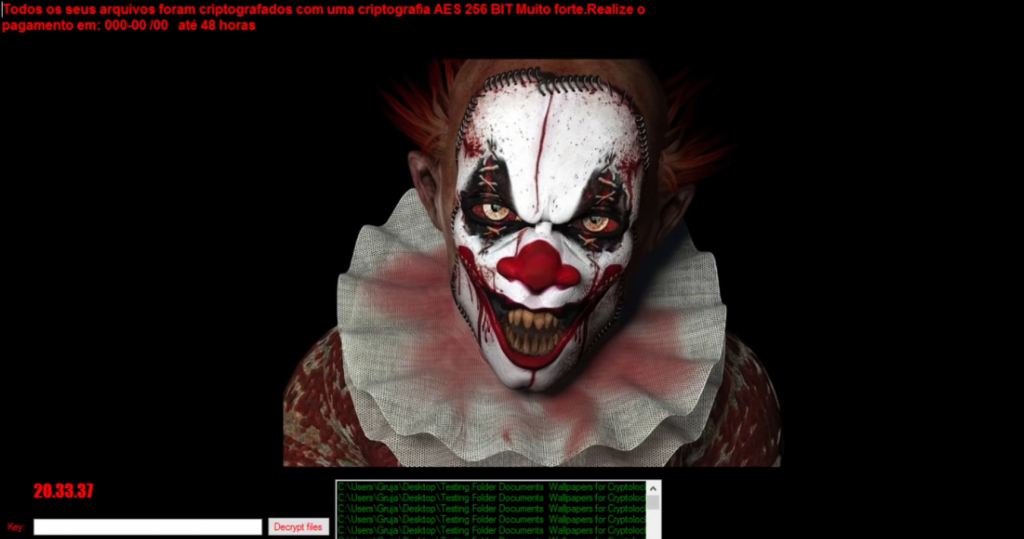
Discovered recently by reverse engineers and cyber-sec researchers, KillerLocker ransomware is most likely a variant of the notorious JigSaw ransomware virus. One symptom that gives the malware away is the design of the desktop screen which the malware changes after infection. It very much resembles the design of JigSaw with the differences being the message written in portoguese and the picture of an evil clown:
The original ransom message employed by KillerLocker is the following:
Todos os seus arquivos foram criptografados com uma criptografia AES 256 BIT Muito forte. Realize o pagamento em:
000-00 /00 até 48 horas
Key: {unique key} Decrypt Files
Você não pode fazer nada sobre isso e sua chave serão eliminadas em 48 horas. Arquivos encrypt
If you translate the message, it is understandable that the virus gives 48 hourse deadline and threatens to delete the decryption key used to unlock the encrypted files if the ransom demands are not met.
When the infections with this ransomware begin to occur, it may provide an e-mail for contact or a BitCoin wallet along with detailed instructions on how to pay the ransom. For the moment, the ransomware may still be on sale in the DeepWeb markets, meaning infection rate with it are expected to rise soon.
After it attacks the victim computer, the KillerLocker virus attacks the following types of files:
xls, .xlsm, .xlsx,.jpg, , .docx, ..pdf, .doc, .docm
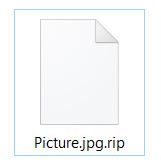
After it attacks the encrypted files, KillerLocker employs an AES-256 cipher on their source code, rendering the files no longer usable. The icon of the files is removed and the file extension .rip is added. An encrypted file by KillerLocker may look like the following:
How Is KillerLocker Spread
The virus may take different approaches for successful infection. It may use spamming e-mails that resemble linked in friend requests or important e-mails with attachments that are it’s payload. Fact of the matter is that KillerLocker ransomware’s spreading core competence and bottleneck is not the virus itself or how it spreads. It is via what type of obfuscator or exploit kit it is distributed, because from this malware depends the outcome of the infection – success or failure.
Remove KillerLocker Ransomware and Try to Get The Files back
In order to get rid of KillerLocker, malware researchers often advise that the best method is via scanning your computer with an advanced anti-malware software, since it automatically scans for KillerLocker’s files and objects it has created and deletes them so you won’t have to spend the time doing it.
Furthermore, the virus is also focused on creating registry objects and defensive tools that may make it prevent you from accessing your computers, such as setting up a LockScreen. This is why it is strongly advisable to enter in Safe Mode while scanning your computer as well.